The year 2017 suffered the greatest ransomware attack in the history of the internet. The WannaCry ransomware detected in hospitals of the UK. It then exploded across the globe and affected more than 200,000 computers across 150 countries. This attack targeted the computers running with the Microsoft Windows operating system by encrypting data and demanded a ransom payment in bitcoin currency. This cyber attack damaged the global economy by billions of dollars.
Moreover, there were around 2181 healthcare breaches, between 2009 to 2017 and each one of them has compromised at least 500 records, according to HIPPAJournal.com. These breaches have entirely exposed 176 million healthcare records, which is roughly half of the population of entire America.
The numbers illustrate that cybersecurity is a major issue in the healthcare sector and that it should be the top priority of the industry to implement security measures and take steps towards the protection of data.
Beyond cyber threats and attackers, there are other problems which cause serious security breaches.
-
Mobile Devices
The adoption of mobile devices in the healthcare sector is on the increasing end. However, most of the mobile and tablets fail to meet the security standards which makes them vulnerable to malware and hackers.
Anthony Giandomenico, a senior security strategist and researcher for Fortinet, tells in an interview with HealthTech “Most of the users don’t know that their phones are as unsafe as their desktops and laptops, which, in turn, lowers their guard when determining if, for example, an email is legitimate or not.”
In an independent survey of 600 mobility professionals working with industries in healthcare, financial services, and public sector, it was found that “More than a third of healthcare organizations (35%) entities said they had suffered data loss or downtime due to mobile device security breaches.”
How to protect mobile devices?
- To prevent a data breach through mobile devices, healthcare providers should encourage users to employ basic cyber hygiene when using mobile devices. These hygienes include ensuring apps are up-to-date, installing malware protection on mobile devices and, only connecting to trusted Wifi networks.
- Using network access control can be a smart solution to secure the data. It can scan devices for threats or out of date spyware protection, ensuring the equipment are safe.
- Healthcare organizations should make it mandatory to use a secure platform to exchange patient information. For example, in May 2017, Mary Washington Healthcare adopted TigerConnect with more than 1000 clinicians for secure messaging between the healthcare professionals and the patients.
-
Employee Mistakes
Two reports clearly show that employees are one of the biggest threats to healthcare data security; Verizon’s 2018 cybersecurity report which examined 1,368 healthcare data security incidents in 27 countries found that 28 percent of all data breaches come from the inside.
Meanwhile, the results of a healthcare data security survey conducted by Accenture showed that nearly one in five healthcare employees would be ready to sell confidential patient data to a third party for a meager amount. These are the people who get jobs in the healthcare industry for the sole purpose of stealing confidential data.
If any data breach happens either due to employee carelessness or malicious intent, it adversely affects the image of the hospital or the organization. These are considered twice as costly and harmful in comparison to external threats.
How to mitigate them?
- Thorough background checks should happen during the hiring process to avoid insider threats.
- All the employees who have access to the critical data should get educated on cybersecurity best practices and the risks associated with unsolicited activities.
- Workshops should be conducted on improving the work ethics of the employees.
- Implement solutions that allow top management to identify security threats quickly.
- Also, organizations should audit all devices used by the staff members as audits are more of a reliable way to look at the usage history of every individual.
-
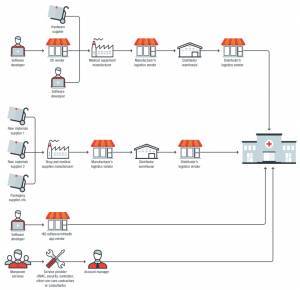
The Supply Chain
Source: Helpnet Security
The supply chain is no longer a stranger to cyber threats. As the healthcare industry heavily relies on cloud-based systems, third-party service providers, and vendors in the supply chain. The organizations also realize the risk of supply chain attacks. Hackers can compromise third party goods and services to steal private data, install malicious code or bring counterfeit devices into the organization. The ISTR noted a 200 percent rise in this type of attack.
Researchers highlight multiple entries that threat actors can use to exploit the hospital supply chain. The potential one is the device manufacturer; a hospital or medical facility has no idea whether the devices they use meet quality and safety standards or get tampered during the manufacturing process as, they lack insights into the manufacturing unit, distribution centers and shipping companies.
Supply chain threats are also rising due to the lack of cybersecurity practices in place at the outsourcing suppliers. And, cybercriminals look for backdoor vulnerability in the systems of trusted party/business that is either connected with or supplies software or devices to that healthcare organization.
For example, in January 2018, Hancock Health, a regional hospital in Greenfield, Indiana, was hit by the SamSam ransomware. The attacker used the credentials of a third-party vendor’s managing account to access the hospital’s data center and then demanded four bitcoin for them to regain access to 1400 files.
How to mitigate supply chain attacks?
- Healthcare providers should work with trusted partners who meet the regulatory compliances of the healthcare industry.
- There should be substantial contracts prepared with the suppliers, and they should be enforced to fulfill every term and condition.
- Employees should only be given access to the specific data which is required to perform their tasks.
- In case of a supply chain attack, ensure that all employees are trained and equipped with the required tools to minimize the effect of the data breach.
Conclusion
There are many threats when discussing the data security of the healthcare sector, but these three come under the most vulnerable ones. Staying ahead of these threats must be a priority to every healthcare provider. It’s worth reminding that these threats can cost healthcare organizations millions of dollars if found ignored.
Organizations have to allocate funds to tackle these threats if they arise. Hence, spending a considerable amount to build a solid foundation to prevent such threats will likely be much cheaper than the fallout from a widespread data breach.