One of the big drawbacks to using “secret” or secure messaging is that everyone you want to contact needs to be using the same service. Even when they are, there’s usually no easy way to share something with large numbers of your pals where they’re most likely to see it, in a way that keeps it for-their-eyes-only.
See also: Suddenly, Messages Are Disappearing All Over—On Purpose
You might think that’s a natural tradeoff between security—that is, preventing the wrong people from seeing your texts or photos—and convenience. But Wickr, a service that lets you send secure, self-destructing messages, thinks it has an answer—by letting users post a “fake” photo to Facebook that will lead other Wickr users you trust to the real thing.
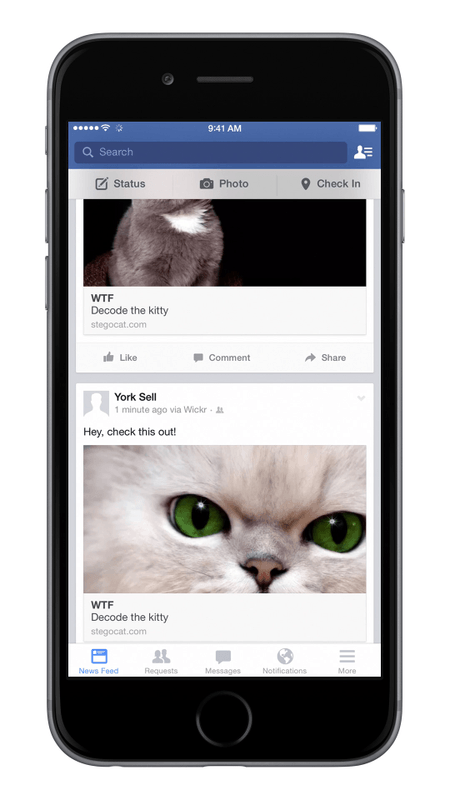
Starting today, Wickr users on Apple devices will be able to share self-destructing photos with up to 151 of their closest friends using a feature the service calls Wickr Timed Feed, or WTF—and that acronym probably isn’t an accident—that combines cats, ephemerality, and a little sleight of hand. (Android and desktop versions are in the works.)
WTF, Wickr
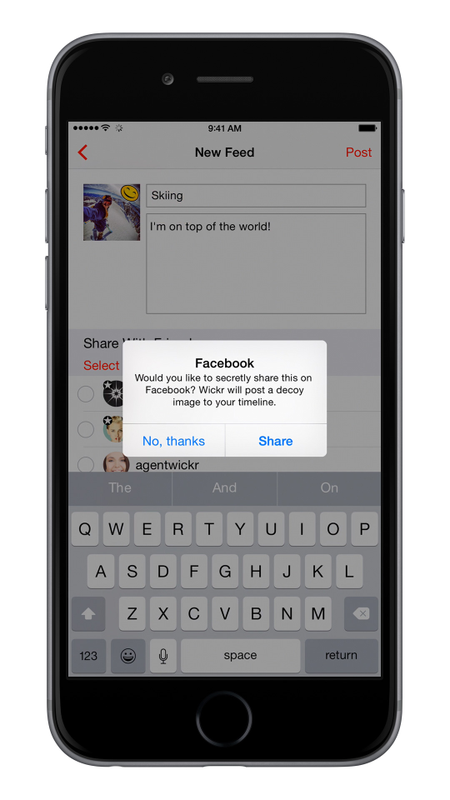
At heart, WTF is basically just an ephemeral photo-sharing service that lets users annotate and share snaps that will self-destruct in 24 hours. This is not too different from Snapchat, although Wickr uses security techniques designed to keep the photos from sticking around after they’re supposed to disappear.
What’s new is the way WTF aims to let you post private photo feeds on Facebook so that only your intended recipients can see them. When you share a WTF feed with other Wickr-using friends, it will ask if you want to post it on Facebook. If you do, the service will post a random cat photo instead of what you’re actually sharing. Clicking on that photo will open up Wickr, where the friends you’ve shared with will be able to see the hidden message. Everyone else on Facebook sees only the decoy cat photos.
Here’s Wickr’s promo video of the feature:
https://www.youtube.com/watch?v=A0-wBc_Lv5A&feature=youtu.be
Security Hype 101
WTF is a clever way of snaking around the usual security/convenience tradeoff, but it’s not completely foolproof. It also doesn’t quite live up to Wickr’s security hype.
Wickr has claimed the hashtag #stegocat for this campaign, since it considers WTF an example of steganography, an ancient technique in which secret messages are hidden in plain sight. Some modern examples of steganography include hidden pixels in printers which reveal printer serial numbers as well as time and date stamps, digital watermarks used in ebooks, and, of course, Russian spies who were caught hiding secret images in photos.
Wickr Timed Feed, though, isn’t really steganography; the shared images aren’t embedded within the decoy kitty pics. Instead, they just link back to the Wickr app itself. That doesn’t really affect how the service works. But it’s a little unsettling when a service that prides itself on its security chops feels compelled to co-opt a technical security term in a misleading way for marketing purposes.
In a similarly disconcerting fashion, Wickr has long billed itself as a good privacy app for human rights activists working to fight dictators, claims that are difficult to verify. Unlike competitors such as Silent Circle, Open Whisper Systems, and CryptoCat, Wickr uses proprietary cryptography, making it difficult for security experts to assess the quality of its code—or to know if anyone has built secret back doors in it.
Wickr CEO and co-founder Nico Sell says the startup used proprietary code to give itself a commercial head start. She points to four independent security audits the app has passed, as well as Wickr’s large hacker budget and $100,000 bug bounty for anyone who can find vulnerabilities that severely impact users.
Wickr has recently added a feature on its app in which users can verify each other’s identities by reading their personal key codes via video, and is working on revising a white paper properly documenting its security protocols in response to feedback from security experts.
What Facebook Knows
Sell says she got the idea for WTF from her daughter. “I have two kids, and one of them is a teenager, and a couple of years ago, she said, ‘Hey, Mom, I know you don’t approve of Facebook, but I’d love for you to find a way for me to use it safely,’” Sell recalls.
Of course, convincing users that it’s OK to post secret—read, naughty or gossipy or otherwise revealing—photos on Facebook, even disguised as cat photos, could take some doing. Sell argues that Facebook only sees who’s using Wickr, but not what they’re sharing.
“Facebook is only going to own the pictures of the kitty cats,” Sell says. “Their servers will never see your real pictures.” WTF offers one further advantage: It lets Wickr users share with more than ten people at once, sidestepping a limitation in the direct messaging app.
As with most other “ephemeral” messaging services, it’s also still possible for Wickr users to screencap secret photos or to make permanent copies using another camera. But Sell argues that any ephemeral protection is better than none.
“It’s not usually in the beginning of a relationship where someone is trying to screw you over, right?” she says. “It’s a lot further down the line.” Which makes a kind of sense, although you could also argue that receiving a bunch of short-lived photos from a new romantic partner might just increase the temptation to save them off.
Lead photo by Jessica Keating Photography; other images courtesy of Wickr

















