Another day, another Android app scare. This time, the app in question isn’t a Russian-created Trojan that drains bank accounts but rather an innocent-looking clone of the “Snake” game called “Tap Snake.” However, Tap Snake isn’t just a game. It’s actually client software for a commercial spying application called GPS Spy.

Used in combination with Tap Snake, GPS Spy can monitor the physical location of the mobile phone with the game installed.
Updated with Google’s comment, see bottom of post.
Not A Major Threat
As scary as it sounds – mobile spyware! – the threat isn’t as bad as it seems, say security researchers.
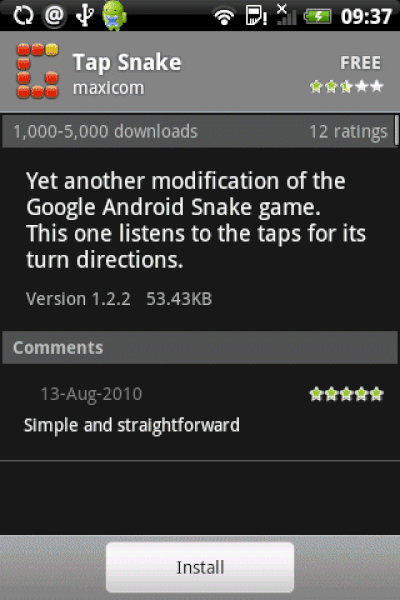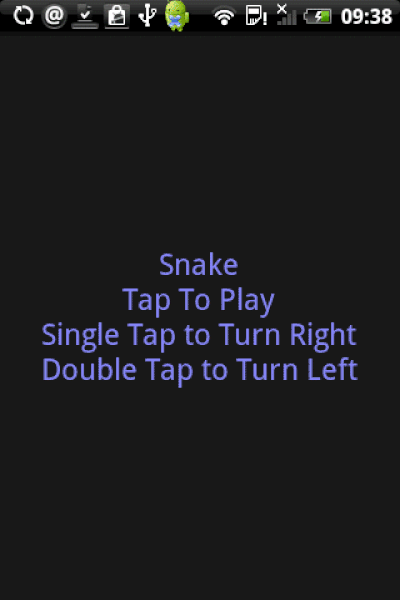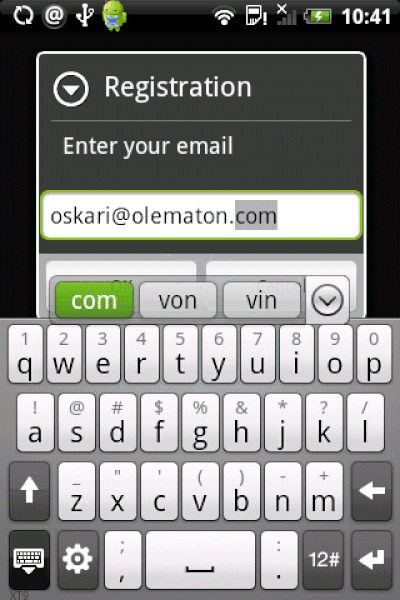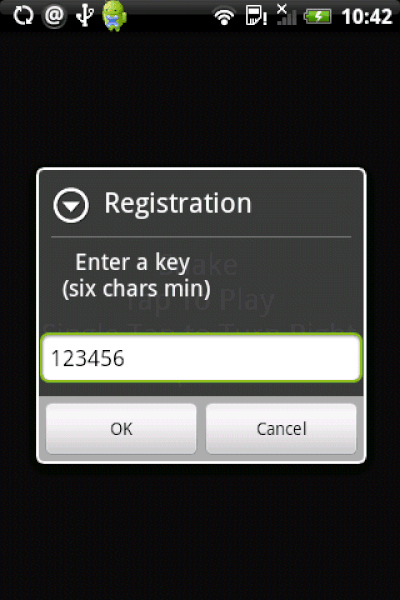
If you were just looking for a “snake” game, and ended up with “Tap Snake,” the permissions it requires upon installation should have been a warning flag. Access location? Access the Internet? Why would a game need that? Why is the satellite icon (GPS) flashing when you play the game? Etc., etc.
These would all be warning signs to a savvy smartphone user that the game in question may be doing more behind the scenes than it should.
How Tap Snake/GPS Spy Works
But the victims of this game aren’t likely to be savvy technical users – just regular ones.
After allowing another person to access their phone, either knowingly or not, the victim would have discovered that a new game had been installed on the device. What they wouldn’t realize is that the simple snake game had two hidden features.
“First,” explains security firm F-Secure via blog post, “the game won’t exit. Once installed, it runs in the background forever, and restarts automatically when you boot the phone. And secondly, every 15 minutes the game secretly reports the GPS location of the phone to a server.”
In order for the actual spying to occur, however, the perpetrator would need to purchase GPS Spy, $4.99 mobile spying application that is registered with the same keycode or email address as Tap Snake. Because of this requirement, they would have needed to first gain physical access to the device being monitored.
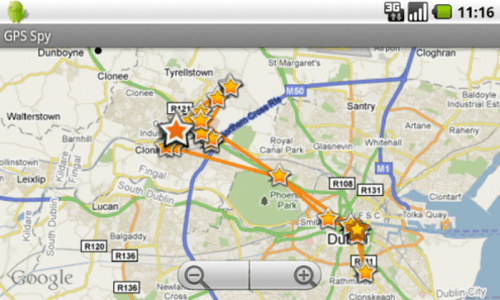
The GPS data transmitted between the two apps is stored on Google’s free App Engine service, says Symantec, the security company which initially outed the malicious code as AndroidOS.Tapsnake on Monday. GPS Spy can then download the data and display it on Google Maps for easy tracking. Each mapped out data point even includes a data and timestamp along with latitude and longitude coordinates.
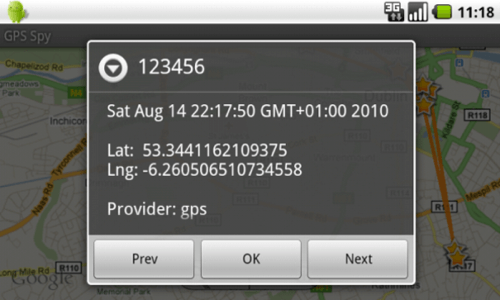
Symantec says it decided to classify this app as a Trojan because it does not disclose its primary purpose up front, and instead masquerades as an innocent game. Still, it acknowledges that using it for spying would have probably required “a dash of social engineering as well – something like, “Hey, let me show you this cool game.”
Android Users Just Need to Pay Attention? Is Security the End User’s Job?
Security firms are advising of the threat but also noting that it’s not a major one nor is it likely to be all that widespread. Android users, warns the mobile industry news source GoMo News, just “need to pay attention” to the permissions apps require.
That was the same advice Google doled out the last time Android phones were hit by a Trojan, too. “Users must explicitly approve this access in order to continue with the installation,” a Google spokesperson explained. “We consistently advise users to only install apps they trust. In particular, users should exercise caution when installing applications outside of Android Market.”
The problem with this security model, as Windows users could tell you, is that when you leave security up to the end user, problems occur. Microsoft eventually addressed some of these issues with the introduction of “User Account Control” in Windows Vista and Server 2008. It’s now a standard feature in Windows operating systems. “UAC,” as it’s known, is the annoying, but protective pop-up box that appears and then warns end users when programs ask for elevated access.
Is it time for Google to implement its own version of a security warning system, as well? “Warning! This game wants to use your GPS! That’s an unusual need for games like this! Proceed with caution!”
Or would Android users just blindly click through those prompts, like they do on most other applications today?
UPDATE! Google’s official comment on this application:
When installing an application, users see a screen that explains clearly what information and system resources the application has permission to access, such as a phone’s GPS location. Users must explicitly approve this access in order to continue with the installation, and they may uninstall applications at any time. They can also view ratings and reviews to help decide which applications they choose to install. We consistently advise users to only install apps they trust. “