Editor’s note: We offer our long-term sponsors the opportunity to write posts and tell their story. These posts are clearly marked as written by sponsors, but we also want them to be useful and interesting to our readers. We hope you like the posts and we encourage you to support our sponsors by trying out their products.

The safest computer in the world is powered off, located in a mineshaft 20 meters below the earth. Unfortunately, this is also the world’s most useless computer.
Connecting systems together – the point of networking – is antithetical to keeping systems safe. Allowing access to your systems of servers or computers needs to be closely monitored and controlled so you can get things done while minimizing the threats of intrusion or denial of service. A balance must be struck between allowing access via the Internet to services you are running and sharing, and protecting the services you might not want others to have access to.
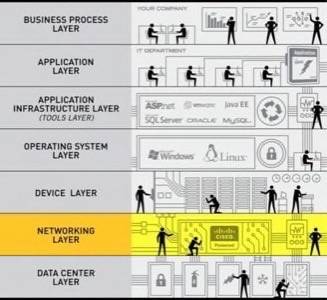
After ensuring a secure data center exists, the next level in the hierarchy of information security, as depicted in the image above, is that of networking. Like a building with multiple entrances and exits, visitors to your network should only be allowed entrance via certain doors. Your network administrator has an all-access pass to your systems so as to limit admittance to network visitors. This is important because just like someone can sneak into a secure building by pretending they’re someone they’re not, it is easy to masquerade on the Internet.
Internet systems communicate via “ports” on servers, which are identified by information stored inside a packet on a network. These ports tell a server how to identify data intended for specific applications. Examples of ports include access to Web servers (typically port 80), another for email (typically port 25), some for Java applications and others for databases.
If you are running a personal blog to share photos and entries, your server would need to allow access to your World Wide Web port so that people could see your site. That same server may have a management application that enables you to upload your photos and entries. That application may be listening on a port that you want to make closed or unreachable to the general public. Using the building analogy, this is the “entrance” to your server you would want hidden or guarded.
This issue presents itself with numerous applications. Email provides a good example. You want to allow email messages to be received, but still protect your server from malicious spam or viruses. The addition of firewalls to your port security can help in this instance. The purpose of firewalls – to keep things out but still let some through – can be calibrated accordingly by your network administrator to provide as much protection as they can. What types of email do you want to allow through? Under what criteria do you judge what is malicious or threatening?
Examining the questions asked above can help establish a secure network to improve the performance of the technology layered upon it, and protect your systems from threats and risk.

















