
It’s been more than a week since security researchers discovered Shellshock, a 22-year-old bug in the bash command-line interface used in Unix by default. Now, we’re just starting to uncover the extent of the exploits hackers have committed thanks to the bug.
See also: Everything You Need To Know About The Shellshock Bug
Web-optimization company Cloudflare has blocked more than 1.1 million Shellshock attacks, the company said in a blog post. Around 83% of these were what it calls “reconnaissance attacks,” digital excursions to scout out vulnerable networks of computers.
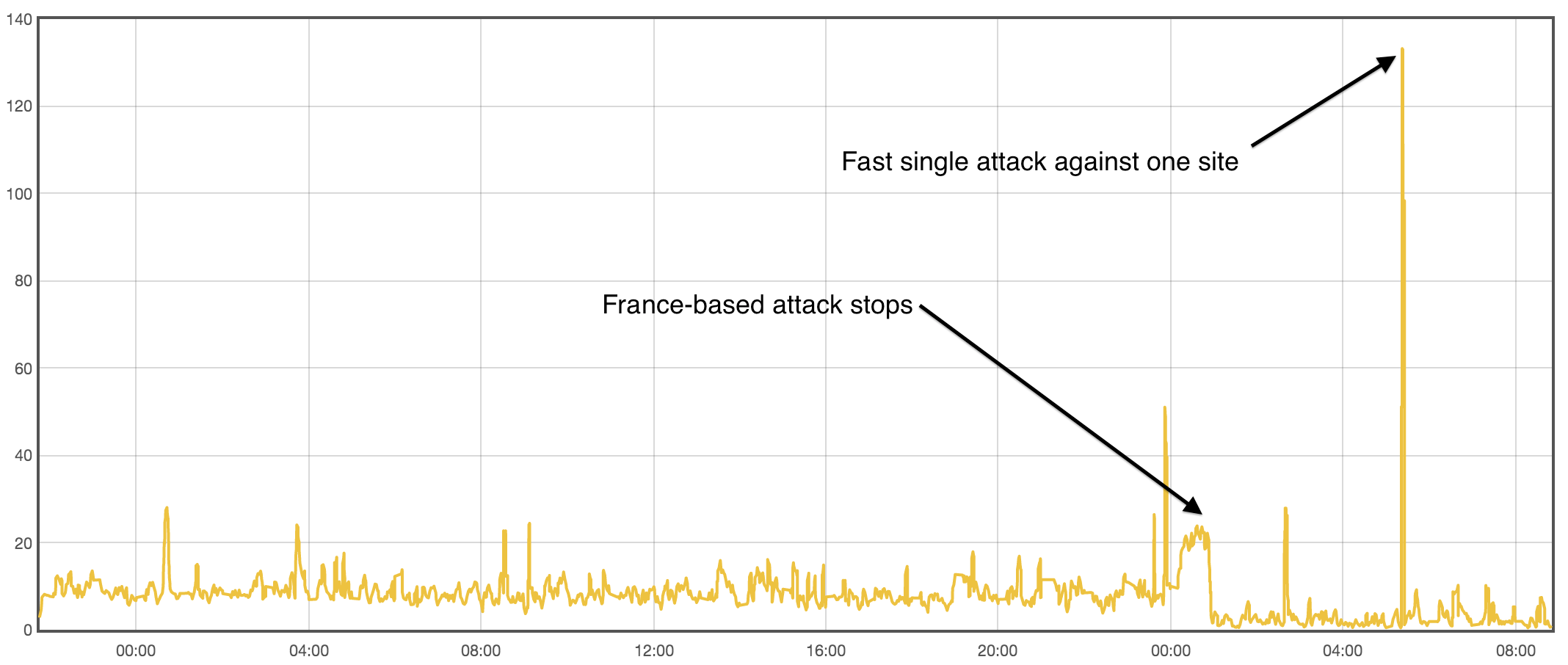
Cloudflare has been closely monitoring the number and origin of Shellshock attacks toward its clients, and released a chart to convey that data. A huge number of attacks were coming from France, but it’s not clear if it’s because the attackers are located in France, or simply routing their attacks through French IP addresses.
Security research firm FireEye discovered another slew of Shellshock attacks coming from an even unlikelier place Wednesday. Using Network Attached Storage (NAS) systems—essentially large scale networked hard drives—hackers could bypass computers entirely while still maintaining remote control over any data found in the NAS.
FireEye said the attacks were targeting devices from a company called QNAP, a popular Taiwanese NAS manufacturer. QNAP has just published a press release urging customers to disconnect their devices from the Internet until a patch becomes available.
See also: Nope! Apple’s Patch Doesn’t Fully Fix The Shellshock Bug Either
Speaking of patches, Apple’s bash bug patch seems to be doing the trick. “The vast majority of OS are not at risk,” an Apple spokesperson has said, and so far that’s been true—even though researchers say Apple’s patch is incomplete. Even as hackers exploit Shellshock on networks and hard drives, nobody has revealed any significant attack on Mac OS computers.
Photo via Shutterstock

















