New malware has invaded the Android ecosystem and this one is creepier than its predecessors. According to IT management firm CA Technologies, the new Android Trojan, titled Golddream.A, has the ability to record phone conversations and store them to the phone’s SD card. The malware has a configuration that may allow it to upload those recordings to a server controlled by the hacker.

Google, Android and the security industry have been battling Android malware constantly in 2011, with DroidDream kicking off the party in late February. According to Lookout Mobile Security, mobile malware has exploded in the six months since DroidDream came onto the scene, with users two and a half times more likely to encounter mobile malware now than they were then. This new Android Trojan is not quite like the main malware that has been seen in the environment this year between DroidDream, GGTracker and DroidDream Light, but the principles of malware and security remain the same whether you are on your computer or a mobile device.
According to CA, the new Android Trojan will download a payload to a smartphone that is triggered when a call is made. The app will record the conversation in “AMR” format and save it to the SD card. Once the malware is downloaded, it will drop a configuration file that has information on how to contact a remote server and the parameters of the app.
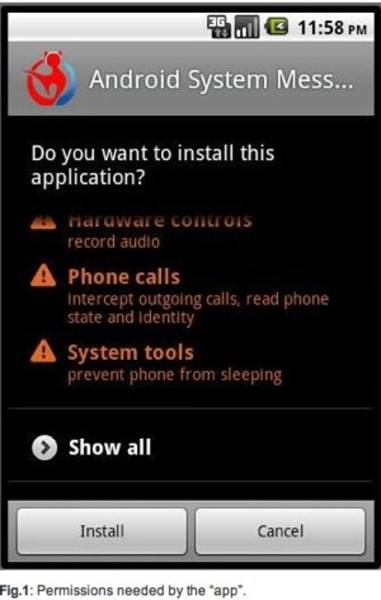
While an app recording and logging conversations is indeed creepy, CA also states that the app “has got many other malicious activities that we have seen in many of the earlier malware incidents targeted for Android platform.” This is where the connection to a remote server is more of a problem than phone conversation recording specifically. When malware invades a phone and gets kernel access, it essentially controls the device. CA did not specifically mention if this application has rootkit access, but if it has any of the capabilities of DroidDream, than it does or has the ability to do so.
This is where a remote server kicks in. Once malware is on a device and has communication with a command-and-control server, that malware can morph and grow as the server sends it more tasks and capabilities. What started as malware that had strange functionality permissions can turn into a device that is no longer controlled by its owner, in the same way that PC malware can make a computer join a botnet.
The best advice for avoiding mobile malware is to check the permissions of every application you download and run it through a security application (that will scan it in transit from market to device) such as Norton, Lookout, Bitdefender or NetQin, among others.