The discovery of the Flame virus earlier this year brought cyberespionage to the international stage. Flame is highly sophisticated spyware, software designed to snoop on infected machines, of unprecedented complexity and scale. But spyware does not need to be created by government-backed hackers to be highly effective. Sometimes simple viruses work just as well. That is the lesson of Mahdi, a new strain of spyware discovered on computers in the Middle East and Iran.
Mahdi (also termed Madi) was discovered by security firm Kaspersky Labs in conjunction with Seculert. The spyware is propagated by a clever ploy known in security circles as spear-phishing. The term phishing refers to using links in social media and email to lure users to visit a malicious website or to download a malicious file. Spear phishing uses the same principle but targets individuals rather than a mass audience.
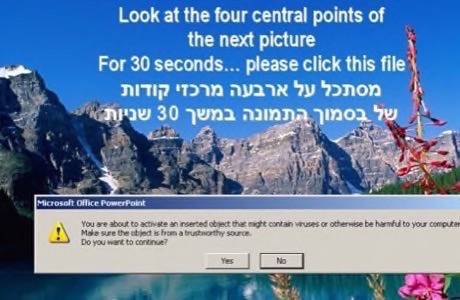
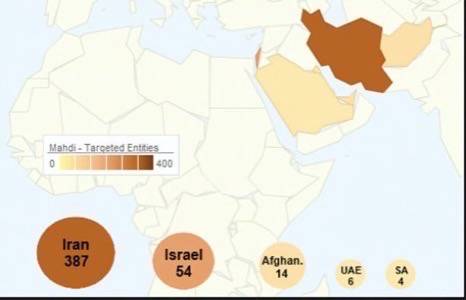
In the case of Mahdi, individuals in Iran, Israel and a smattering of other Middle Eastern countries received emails linking to a specific article or to download a PowerPoint presentation with religious-themed slides. The targets included employees of critical infrastructure companies, financial services and government agencies, according to Kaspersky Labs’ analysis. The lion’s share of the victims were in Iran (387 of 800 known victims) with 54 cases in Israel.
The software reportedly performs the following functions:
- Keylogging
- Screenshot capture at specific intervals
- Screenshot capture initiated by a communications-related event, such as when a user opens up a social networking site like Facebook or uses services like Skype or Gmail
- Backdoor updates
- Recording, saving and uploading of audio files
- Retrieval of data files of 27 different types
- Retrieval of disk structure
- Deletion and binding (not fully implemented)
Given the nature of Mahdi and the targets Kaspersky and Seculert identified, it seems to be a cyberespionage attack focused on specific people in the countries where it has been discovered.
From a technical perspective, Mahdi is fairly simple. It does not exploit any Zero Day vulnerabilities (security flaws unknown to security companies or software publishers), nor does it rely on a complex network of command-and-control servers; only four are known to exist.
This type of attack is much more common on the Web than the gargantuan Flame. Graham Cluley, a researcher for security company Sophos, said that the average user is much more susceptible to “run-of-the-mill malware” than something like Flame.
Dr. Mike Lloyd, chief technology officer of security management company RedSeal Networks, agrees. “Mahdi should remind anyone of the old idea that people in glass houses shouldn’t throw stones,” he said. “This latest malware does not show signs of being complex and expensive, but the relative simplicity of the weapon – compared, say, to Flame – does not mean it’s less effective at reaching its goals. Globally, our infrastructure is weak – there have been steady increases in complexity, and networks continue to become more interdependent.
“Research shows that easy attacks work,” Lloyd continued, “and are at the core of the majority of detected breaches. Attackers do not need major nation-state resources to compromise most defenses. The motivation behind this specific outbreak may be international espionage, but these techniques and others demonstrate how easily defenses can be compromised, including for corporate espionage, theft or acts of war.”

















