Streamlined blogging platform Medium rolled out a new login process Monday that throws the trusty old password out the window. Instead, you simply enter an email address or phone number, and a temporary login link lands in your inbox or phone—just like password reset or account verification links used by sites when you first sign up.
“Passwords are neither secure nor simple,” writes Medium’s Jamie Talbot, summing up a sentiment that has been picking up steam lately. “They’re hard to remember or easy to guess, everyone reuses them (even though they know they shouldn’t), and they’re a pain to type on mobile. They don’t even keep you that safe.”
For being gatekeepers (or bouncers) for our online accounts, they’re inordinately vulnerable. They can be “brute-forced” through trial and error, teased out of you with a cleverly worded email or IM message, applied to access numerous accounts—thanks to our insistence on using the sames ones over and over—and easily leaked out onto the Web. Put another way, they don’t really do a good job of proving that you are who you say you are, and keeping everyone else out.
That’s precisely why companies are hot to ditch passwords and find another way to protect our online accounts—like temporary, auto-generated links or tokens.
The Trouble With Passwords
Password safeguards essentially work the same way: If someone gets access to that alphanumeric word or code, your account is theirs until you notice and swap it out. But that delay can be costly (in more ways than one).
Preventing that nightmare scenario has become a core business for companies like Dashlane, 1Password and LastPass, which manage and hide the bevy of logins in a user’s life behind one secure master password. But these businesses may have to brace themselves, as auto-generated tokens and hyperlinks aim to nix their bread and butter.
Unlike passwords, those temporary links or codes don’t work in perpetuity. They slam the door closed on access after a single use, a set period of time, or often both. And apps and services send them directly to the most convenient receptacles available to you—your email inbox or smartphone.
This approach may seem old-fashioned, particularly when contrasted with newfangled login protocols like face detection, voice authentication and other biometric security, or even creative variations, like emoji passwords.
What the messaging process has going for it, though, is that it’s cheap and easy to implement. And since brute-forcing a token or URL string would be impractical, if not nearly impossible, the system would remove some important points of potential vulnerability.
At least some, anyway.
A Token Effort
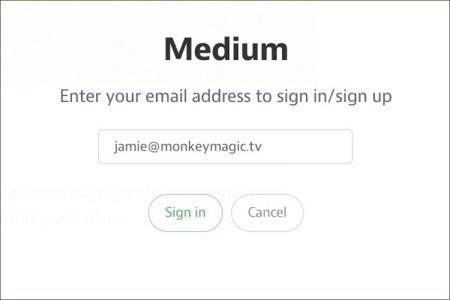
Medium isn’t alone in adopting this rather old-school, simple security alternative. Passwordless, for example, is middleware for Express and Node.js that uses a similar token-based system: Instead of entering some sort of “open sesame,” the keys to your account land in a (supposedly) secure email address or mobile number.
“The classic [username and password] mechanism has by default at least two attack vectors: the login page and the password recovery page.” writes the Passwordless team. “Especially the latter is often implemented hurriedly and hence [is] inherently more risky.”
So nixing the password could actually reduce, rather than increase, risk. In other words, if you don’t have a password, no one can guess it or steal it. Your only vulnerability then is your email.
As the infamous Sony hack—which spilled a mother lode of embarrassing celebrity emails onto the Internet—taught us last year, the relative integrity of those accounts have their own security issues. The temp token approach might amplify them, given that anyone with access to your inbox could theoretically breach your Medium account too.
See also: “Stop Sharing Our Humiliating Emails!” Sony Lawyer Demands
In practice, however, Medium’s system and others like may not actually pose any greater threats. Temp tokens or links expire quickly, and the process itself mimics existing password reset links that Medium and many other services already email or text regularly.
Not that the new password-free systems are hackproof—there’s no such thing—but taking everything into account, they could be a step forward from the username-and-password combination we’ve relied on for so long. At minimum, they appear to be an easy, cost-effective way to remove at least some of the potential vulnerabilities.
When Will We Lap The Old Login?
Of course, password managers are quick to defend the old password system and their efforts at dealing with it.
LastPass representatives were keen to point out to ReadWrite the reduced friction, faster response time and extra privacy you get from its service. (Gmail, for instance, can’t see which services you’re using or send your login emails to spam.)
Ultimately, password wranglers may be but a band-aid for the flawed approach to authentication we’re still stuck with (for now). Eventually, biometric and even behavioral solutions will become more commonplace, and fingerprint or iris scanners—which have already infiltrated some mobile devices—will land on every phone and computer keyboard.
In the meantime, we’re going to need other ways to defend ourselves and our data—perhaps including password-less alternatives like Medium’s. Only when better options become available on a wider scale, can we leave the old ways of logging in behind for good.
Images courtesy of Nikcname and Medium

















