Malware permeated the mobile ecosystem in 2011. The issue is not going away either. Smartphones have an unprecedented amount of personal data that malicious hackers are drooling to obtain. Every day they are coming up with more sophisticated attacks and scheming ways on how to infiltrate that data trove in your pocket.

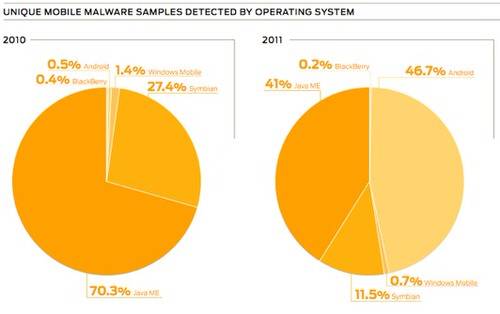
Juniper’s Mobile Threats Report for 2011 shows that malware increased in 2011 by 155%. 46.7% of all threats that Juniper analyzed in 2011 were Android, ahead of 41% for Java ME. While Juniper does not have stats for Apple’s iOS, it does say that there are dangers that could harm your iPhone as well.
From 2010 to 2011, Juniper saw instances of mobile malware in its network rise from 11,138 samples to 28,472. Juniper’s Mobile Threat Center (MTC) examined 793,631 applications across every major mobile operating system. The sources of these applications range from the official mobile OS app stores, third-party app stores, know repositories of malicious apps, malware submissions from customers and partners and “zero day” apps identified by Juniper’s Junos Pulse system.
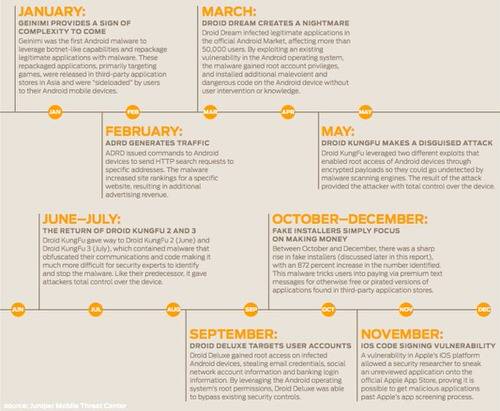
Spyware most common form of mobile malware at 63.39%. Spyware makes sense on mobile devices because hackers are looking for access to contacts, passwords and site activity. Like any spy, malicious hackers want to know as much about you as they can. That information, such as GPS records, text messages and browser history, becomes powerful for malicious hackers looking to exploit the device for monetary gain. In the same vein, the “SMS Trojan” was the next biggest threat at 36.43%. SMS Trojans run in the background of an application and send text messages to premium services owned by the attacker. Many SMS Trojans come from “fake installer” programs, pirated and paid version of free apps (like Opera Mini) that then take over a devices communications channels.
The reason that Android was so popular for malware is because the openness of the Android Market makes it easy for hackers to slip malicious applications in. Google’s “bouncer” has been mostly successful in protecting users but even a malware scanner across the entire Android Market cannot identify zero day attacks. A zero day is a vulnerability that was previously undiscovered and hence difficult to track until someone exploits it. In the last seven months of 2011, Juniper saw 13,302 samples of Android malware, more than the entire mobile malware ecosystem in 2010 combined.
Juniper admits that iOS is safer from malware than any other platform. Juniper notes that those that jailbreak their iPhones are more susceptible to malware and that there are several spoof sites that can jailbreak an iPhone but also leave malware in its kernel.
“There are virtually no meaningful endpoint security products for the iOS platform because Apple does not provide developers with tools to create them,” the report states. “This lack of software protection and a competitive security market leaves users with little protection if malware were ever to make it through Apple’s application vetting process. In the long (term), this could create a false sense of security for Apple users and prove to be an even bigger risk than Android’s open model.”
It must be pointed out that while iOS is safer and indeed lacks endpoint security, it is in the best interest of Juniper (and every other company that provides mobile malware protection) to put pressure on Apple to give the tools to create iOS security apps. There is big money in security and if there is ever a hint of malware on iOS devices, the security companies stand to profit from that.
Other forms of malware that can affect mobile devices include direct attacks, such as SMS spam or attacking applications with malicious content or packets. Applications, by definition, are software and as with any software are open to be hacked by external forces. There is also vulnerability through the browser. Juniper points out that the Webkit engine that is used by Android, BlackBerry, iOS and webOS has vulnerabilities that can be exploited through visiting an infected site.
Connectivity hacks are also vulnerabilities in the system. Connectivity vulnerabilities come from Wi-Fi sniffing on an unsecure network or “man-in-the-middle” attacks where malicious hackers insert themselves inbetween the device and its point of connection to the outside world.
Juniper expects to see more malware come to the mobile ecosystem in 2012. There is just too much rich data ripe for the plucking for malicious hackers to stop their efforts. Targeting applications and payments processors will grow as hackers create ingenious ways to attack user data for financial gain.