Conficker, the Internet worm that caused a mild panic reminiscent of Y2K late last month, but which failed to do anything spectacular that would have warranted the breathless coverage on 60 Minutes (“The Internet is Infected”), has finally woken up. This morning the worm started to update itself via a peer-to-peer network between infected machines after downloading its payload from a server in South Korea.

It is not clear how many machines were infected with this worm, but estimates range from 9 million to 15 million.
While earlier variations of the Conficker worm prevented infected machines from accessing the servers of most antivirus companies, this new variant also blocks access to sites that offer tools for removing the worm like BitDefenders bdtools.net.
Oddly, the Conficker worm now also includes an instruction that tells the worm to remove itself on May 3 (the hackers clearly like deadlines), though after that, it will keep a port open on these machines that will allow the hackers to get back into these computers at any time.

The Big Picture: Spyware, Spambots, Pop-Ups
According to both Trend Micro and Symantec, Conficker, after downloading its update, also downloads a variant of the well-known Waledac malware. Waledac is one of the world’s most active spambots.
Security researchers are still trying to understand the connection between Waledac and Conficker’s new E variant (only a small number of antivirus products can currently detect this version of Waledac, by the way). Some, however, speculate that this connection could mean that Conficker was created by the same group of hackers that created Waledac and its predecessor, the infamous Storm botnet.
Business Model?
According to Kaspersky Labs’ Alex Gostev, Waledac will download a rogue antivirus application onto infected machines, as well as an email-worm that can steal data and send spam. The fake antivirus software will ask users to pay $49.95 for “Spyware Protect 2009,” which, of course, is anything but an antispyware product.
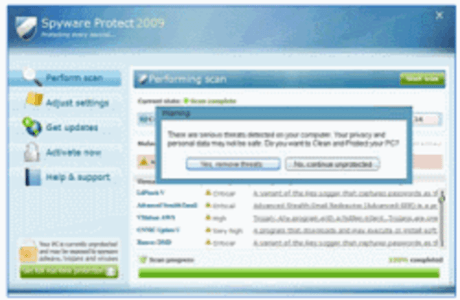
Protect Yourself (and others)
Of course, if your Windows machine is up to date and if you have kept your antivirus software up to date then chances are very good that you are well protected against Conficker.
If you want to learn more about Conficker and how to protect yourself, have a look at this list of resources we put together last month. If you want to see if you are infected, head over to this site from the University of Bonn.
















