Still, remember when your colleague in the office sent you some strange looking email? Or when your favorite email provider suddenly asked you to update your password? Or a recent period when you were battling with slow internet network? All these incidences point to one thing: cyber attacks. IoTGadgets will be exploring behind the scenes motivation and methods of cyber attacks and how they can be curbed.
Who wears the hat?
Not all hackers are cut from the same cloth. Our focus in this post is on the black hat and grey hat hackers, not white hat hackers. The difference between both groups is that white hat hackers carry out their activities for research purposes and with intention to discover vulnerabilities and protect the system from future attacks.
On the other hand, black hat and grey hat hackers carry out their activities with deliberate intention to cause damage to the system. They are the ones responsible for popular cyber attacks like WannaCry, Dyn, US Department of Justice, etc.
Hacks and Attacks
It’s safe to generally conclude that black hat and grey hat hackers are motivated by money. Their sole aim is how to get the fattest pay check from their activities by selling the valuable information gathered. Getting the pay comes in various ways.
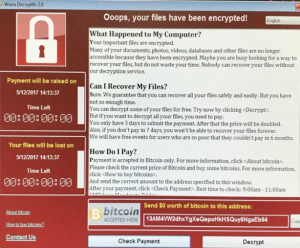
The method adopted by the WannaCry ransomware attack perpetrators was to lock the files on the NHS servers and ask for an amount of bitcoin to be deposited before the locked files are unlocked. The picture below was what users saw on their screen when they tried to access a locked file.
Hackers for hire are employed by governments or large corporations who wish to gain inside information about a rival that of course has not been made publicly available. The Chinese have been accused of trying to hack Google servers with the hope of obtaining information on the US government’s files of suspected spies, terrorists and agents which they have put under surveillance. Such sensitive information if obtained are sold to the highest bidder.
A Distributed Denial of Service (DDoS) attack is when hackers cripple a site by targeting it with traffic beyond its capacity. In 2016, Spotify, Amazon, Netflix, Airbnb and Twitter suffered from the largest ever DDoS attack in the Dyn cyber attack.
How IoT and Bitcoin Comes into Play
Statistics show that IoT and related technology investment will almost double by 2020, at the same time when volume of IoT connected devices will surge worldwide from 900 million to 26 billion. While these should be good news, we should also be worried hackers would take undue advantage.
Most IoT devices come with little or no protection, leaving them vulnerable to hackers who can easily manipulate these devices to become a BITNET, thereby increasing the force of a DDoS attack.
While bitcoin is not necessarily the prerogative of hackers, there is no denying that they are taking advantage of the trustless peer-to-peer payment system of the most popular cryptocurrency. Transactions in bitcoin do not require any input from banks, credit cards or any other third party, effectively promoting the anonymity hackers wish to maintain. Once funds are received, it could be moved around to blur the trail before eventually converting to Fiat.
Mitigating Hacking Activities
Everyone has a role to play if we want to halt the hackers. First is developing safe cybersecurity habits which can only be done through training both at the organizational and individual levels. It’s important people are educated on basic actions like frequently changing their passwords or setting up two-factor authorization (2FA) where available.
Holding manufacturing companies in the IoT industry accountable for complying with cyber security protocols. Fines should be imposed on those seen to be flouting the rules.
Cyber crime reporting and watchdog organizations like Action Fraud should be given more exposure and raised profiles while maintaining their independence. Many are not even aware they exist, accounting for just 7% of data security breaches being reported. The more people know they exist, the higher the reports that could be made.
In essence, while it would be near impossible to stop hackers, the damages they cause can be brought to a minimum. This is because the IoT market is growing in leaps and bounds, keeping track of development is an herculean task, especially as most have low security protocols. This coupled with the anonymity offered by bitcoin could make the task more difficult.