Malware is a worldwide problem. If there is electricity, an Internet connection and a computer, there will be viruses, worms, Trojans and other sneaky programs trying to gain access to your computer. Where do these nasty creatures come from?
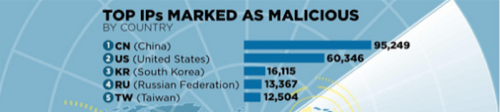
A large percentage of the world’s malware comes from China. According to AlienVault’sOpen Threat Exchange platform, China is the capital of malicious Internet addresses, based on 95,249 addresses analyzed. The United States comes in second with 60,346, well ahead of the third, fourth and fifth malware vectors: South Korea (16,115), Russia (13,367) and Taiwan (12,504).
How is this malware being delivered? The average virus wants to find its way into computers. Direct injection (where a virus is not hidden in a different type of file) is fairly rare. Far more commonly, malware hitches a ride on an otherwise benign file. This is the reason why security programs scan all files downloaded to a computer. The top malware-infested file type is .exe, the most common file type for a Windows program.
The second most common carrier is HTML content, which can be found on almost any Web site as well as in emails. Zip and RAR files, which bundle together other file types, are the third most common, while Adobe PDF and Flash files are also prevalent malware delivery vehicles.
The top types of viruses are all associated with Windows. While Mac malware exists and is becoming more prevalent, the amount of Windows malware on the Internet is nothing short of stunning. The top five malware content types found by the AlienVault community are all derivations of Windows viruses.
Since February, the AlienVault Open Threat Exchange has analyzed over 5 million suspicious URLs. That is a drop in the bucket in comparison to the billions of sites on the Internet, but a large enough sample to provide a sense of how much malware is present on the Web. The company received nearly 30 million entries from its users and found a little more than a million malicious addresses. See the infographic below for more details.
The data was aggregated from AlienVault’s Open Threat Exchange from Feb. 20 to July 20, 2012. The data comes from the company’s customers as well as its Open Source Security Information Management (OSSIM), an open-source security information event-management platform.


















