Mobile handset maker HTC has found itself in some hot water concerning security leaks in some of its popular Android smartphones. HTC’s Android skin “Sense” downloads logging tools onto users phones that can be used to track user accounts such as email, GPS and location data, phone numbers and SMS data and the system kernel. If you thought that the iPhone location data issue was outrageous, HTC takes data leaks to a new plane of existence.

This looks like a case of sloppy development when it comes to Sense. All of the major Android OEMs have tried to differentiate themselves by adding skins to the stock Android experience. The problem for HTC is not the user interface, it is the back end that leaks like a broken sieve.
Android Police worked with mobile security researcher Trevor Eckhart to determine the extent of HTC’s leaking data and found it to be extensive. Eckhart found that an app called Htclogger.apk would allow any app with Internet permissions to open a local port and have access to a multitude of information such as coarse and fine location data, battery stats, Wi-Fi access information, accounts services, device tasks, logs and sync settings and stats. That is just what Android Police found in searching their own HTC EVO.
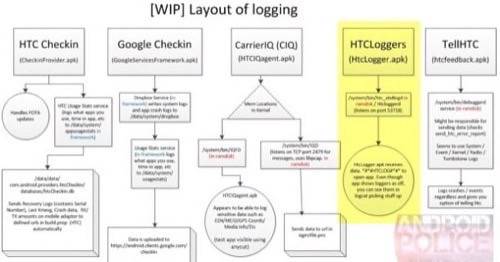
Image: Android Police
On one hand, the actual logging and tracking that is being done on HTC phones is nothing new. Most smartphones, in one way or another, track a variety of device and user behavior. It is how OEMs refine the user experience and platforms create patches and updates to the firmware. The problem here is that HTC Sense has a hole in it that lets that data escape in to the wild.
Eckhart put together a video for the proof of concept for HTC’s security leaks. Take a look at it below.
The EVO 4G was one of the original powerhouse Android smartphones, the first to approach “superphone” status and directly compete for user attention with the iPhone. Has the EVO been leaking user data since it launched? According to Android Police, these vulnerabilities affect any phone using the stock version of Sense.
Many of the popular mobile security programs check a native applications permissions against its codebase to determine if the app is doing what it says it is going to do. For instance, if an app’s permissions are limited to accessing the Internet, then it theoretically should not be able to leak data through an open port. This is a new wrinkle to mobile security that the mobile security apps like Norton and Lookout probably do not have a way to test for yet. If they did, HTC would have been called out long ago.
Do you have an HTC Android phone? Is the interface with Sense worth the potential that a hacker could know everything about you and your phone? Let us know in the comments.