Earlier this week, we reported that a large number of businesses worry that social networking could endanger corporate security, but according to a new report from Palo Alto Networks, social networking is only a minor issue when compared to the proliferation of browser-based file sharing tools, P2P networks, remote desktop access applications, and more sophisticated encrypted tunneling applications like SSH, GPass, and Gbridge.

Palo Alto Networks specializes in providing firewall solutions to enterprise customers, and this study is based on the behavior of nearly 900,000 users on 60 large corporate networks.
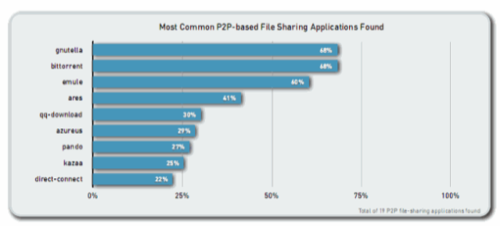
File Sharing
According to this study, users on 92% of the monitored networks used P2P software, with BitTorrent and Gnutella being the most often used services.
On 76% of the monitored networks, the company also found that users used browser-based file-sharing and cloud-storage tools like YouSendIt and MediaFire. According to Palo Alto Networks, tools like MegaUpload, docstoc, Box.net, and Zoho Writer might seem extremely useful to a user who wants to finish an important document at home, but these services also introduce a number of business risks, including a potential lack of compliance.
Employees Will Find Ways to Route Around Corporate Security
The study also found that users will go to great lengths to route around corporate networks and often use tools like Gbridge, encrypted tunneling applications, and various private and public proxy services to circumvent security protocols, corporate firewalls and filtering mechanisms. Companies are spending a lot of money on firewalls and filtering products, but in the end, users will always find a way around these.
The conclusion of this report is pretty straightforward: application developers are making it easy for users to negate corporate firewalls, and users are happily taking advantage of this, while corporate IT networks are constantly playing a cat and mouse game with these users. Palo Alto Networks is obviously in the business of selling better firewalls, so the company’s recommendation to filter traffic not by ports, protocols, or IP addresses, but by application type, content, and user doesn’t come as a surprise. Some users, however, will always find a way around these systems.
It is important to note, though, that this study also shows that there is clearly a large demand for these kinds of cloud-storage and browser-based file sharing services, and a lot of the risks detailed in this report could be managed rather easily by giving users access to a comparable set of approved tools.

















