
In 2009, security company Symantec noticed a particularly complex malware code infecting users’ computers. At first the company did not think much of it outside of the fact that is was unusually complicated. The company wrote detection and repair codes for it. Once detected, malware usually shrivels and dies. Yet, the malicious code, known as W32.Xpaj.B, did not go away. It morphed and evolved, allowing one group of cyber criminals to use it for years to perpetrate a search engine click-fraud scheme that netted the hackers an easy $62,000 from unwitting advertisers.
Symantec was able to track down the command and control servers that were running W32.Xpaj.B and did a full breakdown on how the scam worked. The results were surprising – a complex code working on top of a simple infrastructure – and showed how easy it is for criminals to set up malware workshops and watch the money roll in.
Simple Tech Turned Into Click-Fraud
Symantec wrote a white paper on their findings on W32.Xpaj.B. The virus itself is a classic file that injects itself into other executable files in an attempt to spread through the computer. It has clever bits where it tries to hide detection by using a code mingling approach to obfuscate its signature from the entry point to a file. See picture right.
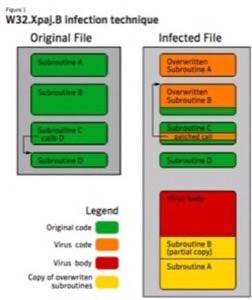
Once in a computer, the virus will check if it wants to stay there. If part of the code detects a .mil, .gov or int hostname, it will exit the system. Also, the virus will check the host country of the infected device and will exit if it finds it is in one of seven Eastern European countries: Russia, Uzbekistan, Belarus, Kazakhstan, Krygztan, Ukraine or Tatar. Symantec tracked the C&C servers to the Kiev, Ukraine and believe the programmers told the virus to exit those countries to avoid detection by local law enforcement.
Working the Ad Model
W32.Xpaj.B works in the pay-per-click advertising structure. It hijacks users’ search queries and clicks through to a fake search engine with results returned that are actually advertisements, not legitimate results. It then makes money when the user clicks on those links.
Sound simple? It is. Also, it is not.
Computers infected with W32.Xpaj.B will effectively add several layers to what is a normal search query. Those first steps are easy.
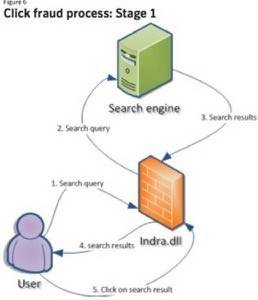
It is after that point where things gets more complex as the query and the users’ computer are redirected several times to reach the fake search engine, which will eventually send it advertisements the programmers want the user to click. The C&C servers contain PHP apps whose script will parse the POST (search) request from the DLL client. If the search term goes through the process clean (and is not bounced out of the process through various IP address associated with search engines) then it is decrypted and extracted. The search term is then submitted to par-per-click ad sites.
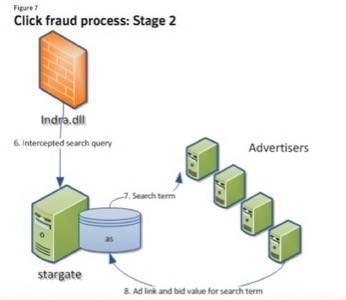
It is not done yet, though. The results are sent to the user’s computer and the one of the programmer’s servers passing through a referrer page. For the user and the advertiser it looks like a click was made from a legitimate transaction. Yet, the programmer has defrauded the advertiser.
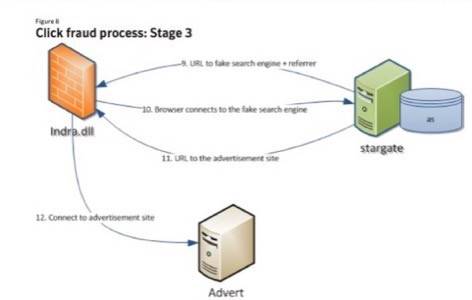
Low Barrier For Entry
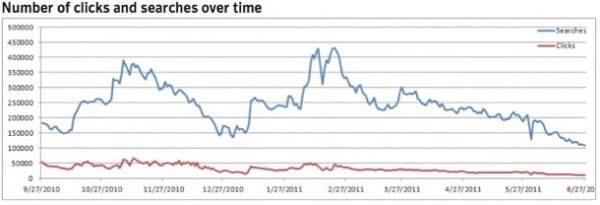
Through this process, over a period of Sept. 27, 2010 to June 27, 2011, the programmers made on average $170 per day (ranging for $43 to $450) with the cycle of money gradually declining as the virus was eliminated from more computers.
Symantec shows the example of W32.Xpaj.B as how the barrier for criminal fraud on the Internet has been set alarmingly low.
The threat and associated infrastructure, in relative terms, are not complicated. The scheme involving referrer values and redirects in an effort to avoid fraud detection is complex, but the technology used is quite basic. There are several versions of the Web applications on the servers and while the code is growing more sophisticated, it is still very basic. It was only the most recent iteration that utilized an SQL server and even that is done in a primitive manner. The database is effectively used as a flat file format, with no normalization of the schema or database optimization. This simplicity is in stark contrast with the complexity of W32.Xpaj.B, the initial reason for this research.
This is an overview of the findings from Symantec’s white paper. If you’re interested in further information, check out the company’s blog for more details.

















