Amid the hubbub over new iPods and iTunes’ LPs announced at last week’s annual Apple event, one feature that was a little under-hyped was the new “anti-phishing” protection built into the iPhone’s Safari web browser. The added feature, available via an iPhone software update, warns users when visiting fraudulent websites using Safari. This sort of technology is already commonplace on the web, but is rarely seen on the mobile platform.

Unfortunately, there seemed to be a problem with the new security feature: it wasn’t working…or at least, so it seemed. As it turns out, the problem was that users weren’t informed as to how to properly activate the anti-phishing protection, an issue that points to a poor implementation of what could and should have been a major breakthrough in mobile computing technology.
The Problem: Anti-Phishing Protection Doesn’t Appear to Function
Although Apple touted the anti-phishing protection back in March when they announced their 3.0 update, the new feature didn’t actually materialize until this month when the company released the OS 3.1 iPhone/iPod Touch software. According to Apple, the anti-phishing protection feature will display an on-screen warning message when you attempt to visit a known malicious website.
Once the update was released, security researchers and other Apple enthusiasts began testing the new technology. The results were immediately disappointing. “I’ve not been able to get it to block anything,” Michael Sutton, vice president of research at security firm Zscaler was quoted as saying. He had been testing the feature using known phishing websites identified by the anti-phishing database hosted at PhishTank. The Mac Security Blog also found after extensive testing that it simply “does not seem to work.” MacWorld, however, found that the feature worked sometimes, but the inconsistency hinted that the technology was not “ready for public consumption,” they reported.
What gives? Did Apple really release a broken feature? Were they even aware of the problem? Blogger Jim Dalrymple of The Loop decided to go straight to the source: he asked Apple.
Apple Says “You’re Doing it Wrong”
Apparently, this was not a case of the anti-phishing technology being broken. It was a case of everyone simply “doing it wrong.” As it turns out, in order for Safari’s anti-phishing database to update, there are a few particular steps that need to be followed, explained an Apple spokesperson. After updating the phone to the OS 3.1 update, users need to do the following:
- Launch the Safari web browser.
- Connect to a Wi-Fi network.
- Charge the iPhone with the screen off.
The spokesperson added that for “most users” this process should happen automatically when they charge their phone. We would have to disagree. “Most users” don’t launch the Safari browser prior to charging their device – if anything, they close down any open applications before plugging in the phone to charge.
Poorly Implemented, Poorly Explained
If you follow the above steps, the feature will work. However, most users will never know to do this unless they happen to closely follow technology news and blogs. The general mainstream population – the very demographic Apple so craftily attracts via their billion dollar marketing campaigns – expects things to “just work.” That is the Apple promise, after all.
Yet even on Apple’s own website where they detail the various new features in the OS 3.1 update, there is no mention as to how the anti-phishing protection should be utilized. It simply lists that the feature exists. A helpful link to a “how to” guide would seem appropriate here or, at the very least, a footnote.
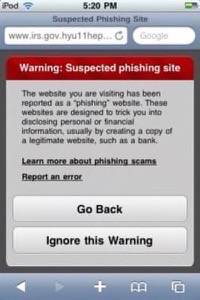
Having to perform the somewhat unintuitive stepsto get the anti-phishing protection feature to function properly seems like an unusual miss for a company who generally makes things simple and straightforward. Why does it need Wi-Fi, for example? Apple claims that the Wi-Fi connectivity is required so as not to incur any additional data fees for the end user. But launching the browser? We almost wonder if it wouldn’t have made better sense for Apple to implement the feature in the new iTunes update instead. The desktop software could retrieve the updated anti-phishing database from the internet upon launch and could then sync it to the iPhone or iPod Touch the next time it was plugged in. That would also alleviate another common problem with the current implementation – if the phone isn’t plugged in long enough, the update won’t complete and users will only be partially protected. On the other hand, the inclusion of the database via a sync would have ensured that all the data was copied over to the phone.
In the end, though, Graham Cluley, a senior technology consultant at Sophos, reminds us that maybe we shouldn’t be too hard on Apple. “Many other smartphones don’t offer even the most elementary form of anti-phishing protection to their users,” he says. That may be true but, unfortunately, the way Apple chose to deliver their anti-phishing protection feature means that most iPhone users won’t be protected either.

















