If you’re looking for new, but obvious, ways to cut government waste, try this: According to a cloud computing strategy report last February by U.S. Chief Information Officer Vivek Kundra, government information systems today may be using less than 30% of their available server capacity. And while trying to take inventory of the various information assets that may be under-utilized, Kundra and government researchers are discovering that agencies presently lack the tools to make any kind of thorough inventory of what assets they already have.

This is the environment that Amazon Web Services is trying to address, with today’s announcement of a new special administrative district, if you will, of its cloud. Called AWS GovCloud, it’s designed to handle the specific requirements laid out by Kundra last February, including compliance with the Federal Information Security Management Act of 2002 (FISMA).
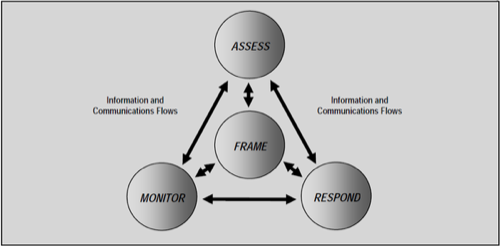
Last March, the National Institute of ScienceStandards and Technology spelled out the government’s new approach to orienting government information security around risk management (PDF available here). It’s a four-stage approach whose objective is to create a new mindset for risk management, as conveyed in this diagram:
1. Frame the context of risk assessment in a new way
2. Assess risk in terms of the individuals who have specific responsibilities for addressing risk areas
3. Respond, and plan to respond, to risk management events with prescribed courses of action with relevant workflows
4. Monitor risk over time using real-time tools
For government services to be moved into the cloud, they needed to be able to utilize assessment and monitoring tools that catered to the specific needs spelled out by NIST. Over 100 government services have already utilized AWS’ first stage of trials, according to the company, and GovCloud represents Amazon’s official recognition and implementation of the policies and procedures learned through those trials.
“The Federal Government will create a transparent security environment between cloud providers and cloud consumers,” reads Kundra’s report. “The environment will move us to a level where the Federal Government’s understanding and ability to assess its security posture will be superior to what is provided within agencies today. The first step in this process was the 2010 Federal Risk and Authorization Management Program (FedRAMP). FedRAMP defined requirements for cloud computing security controls, including vulnerability scanning, and incident monitoring, logging and reporting. Implementing these controls will improve confidence and encourage trust in the cloud computing environment.”
In terms of potential cost savings, Kundra cited an early 2008 trial of a cloud-based CRM application for the Army Experience Center. Although contractors had bid over $1 million to replace the AEC’s existing software, the cloud-based trial ended up costing about $54,000.

















