Since FinTech apps deal with highly sensitive personal and business data, security should be at the forefront of finance and banking solutions development. However, the reality is different. Here’s what it takes to build a highly secure FinTech application.
Data storage issues, weak encryptions, data leakages, are just some of the vulnerabilities frequently discovered in FinTech applications.
According to the State Of Application Security Report by Immuniweb, 98 of 100 reputable FinTech startups are vulnerable to phishing and hacker attacks. These figures spill the light on a serious issue: an entire industry, which should be 100% secure and dedicated to protecting clients’ data.
But the fact is that the data is an easy target for cybercriminals. The notorious example of Equifax, responsible for some of the most significant data breaches in history, and, most recently, Earl Enterprise, proves that neglecting security can be devastating.
The data uncovered by independent investigators brings troubling news: some of the most popular FinTech mobile apps are insecure and virtually expose their users’ data to the risk of theft.
Under these circumstances, building secure FinTech apps with data protection in mind is not only a hallmark of a responsible and trustworthy company but will also give your FinTech application a distinct advantage over competitors. Below we will guide you through the steps you need to take to build a secure FinTech solution.
How to create secure FinTech solutions.
Ensuring FinTech app security will require you to include some of the important phases into every step of the development process. Here’s how to secure your FinTech app.
1. Build infrastructure security.
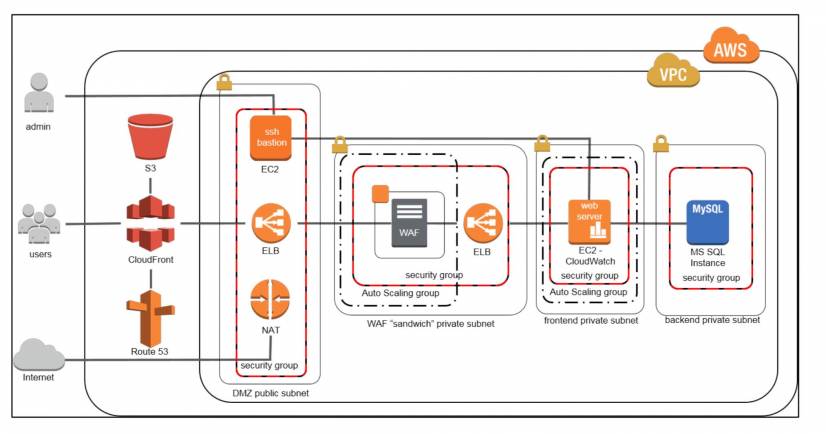
The FinTech app you’re developing will have to leverage quite a robust IT infrastructure. At the initial phase, building a secure infrastructure is of paramount importance. If your app runs on the public cloud, choose a reputable cloud vendor who is serious about security and complies with modern cloud security standards.
AWS enterprise cloud, for example, has all it takes to stand up against massive DDOS attacks. It will also ensure fast disaster recovery in case of disruptions.
For financial institutions building their FinTech apps on cloud infrastructure, it’s also critical to make sure that cloud vendors comply with the same standards they are using internally.
2. Build a secure application logic.
Simply put, building app logic with security in mind means integrating security into every step of the application usage process. From data storage to password complexity, each facet of your future application has to be protected against possible threats.
What data has to be stored within the application? Is it really necessary to store all debit and credit card numbers? Who’s going to have access rights to certain application features? These are the questions you need to ask during the early development stages of your FinTech application.
The best practices for building secure FinTech solutions include:
- Introducing complex passwords.
- 2-way authentication.
- Keeping a log of every action the user performs as well as their geolocation, IP address, and device info.
- The multi-step approval process for all critical activities.
- Monitoring transactions and blocking the ones that seem suspicious.
3. Write secure code.
The code of a FinTech app has to be easily transferable between devices and include algorithms for easy detection of any flaws in case of a breach or an attack. It also has to be easily updatable if the worst-case scenario takes place.
The best practices for writing secure app code include input validation and reviewing any data that is being sent to external networks. Monitor the granting of access to only the most basic app functions and define clear access rules, taking measures to ensure adequate protection of sensitive data.
Other measures would include protecting your code from SQL infusions, which are still an easy way of hacking a FinTech app.
4. Test your FinTech solution.
Needless to say, building secure FinTech solutions requires thorough testing during each of the nine above mentioned stages.
The generally accepted practice is to carry out “penetration testing” – running your own faux attacks to detect vulnerabilities within an app. Needless to say, continuous and meticulous testing should be an integral part of the development process. Hire security testers, if you need to, to build high-quality, attack-resistant code.
The standard testing process for FinTech companies includes seven consequent steps and starts with the requirement gathering and review. This is necessary for the QA engineers to understand the basic requirements and the security standards the particular FinTech solution is expected to adhere to.
All in all, the steps are as follows:
- Requirement gathering.
- Requirement review.
- Preparing business scenarios.
- Functional testing.
- Database testing.
- Security testing.
- User acceptance.
After they have a clear understanding of the app security requirements, QA testers work on figuring out every possible business scenario which may potentially open a doorway for an attack or data breach. An understanding of FinTech sub-niches like insurance, banking, or investment is needed to list these action sequences and test them for security loopholes.
The next step is functional testing, which, for FinTech organizations, is a complex process in itself. Using FinTech apps presupposes an interchange of money and personal info, so QA engineers should work through every possible scenario. Further on, they proceed with database testing, security testing of APIs, identification, authentication, and authorization. The final step is the user acceptance testing when the app and its core functions are tested from the user perspective.
5. Ensure web-server security.
A web server is the most frequent target for external attacks. It’s now a common practice to protect users’ data with an HTTPS SSL certificate. Most popular browsers will alert users if a website has none – so, you obviously can’t omit this step and be deemed trustworthy.
Using VPN is another common practice — it does add complexity at the setup phase, but since it only grants access to hardware with a valid public key, so it’s worth the effort. Neglecting web server maintenance may also cost you dearly: run regular check-ups of all web server components and hire a professional DevOps consultant if you need one.
6. Secure every step of your daily workflow.
It is mandatory to reduce the human factor – the common cause for almost half of all security breaches, according to Kaspersky. Take measures to ensure a fast and easy recovery. Introduce regular backups of all data, files, and code, practice security rehearsals.
Simulate potential emergency situations and act out ways how your personnel will handle them.
Set up clear and coherent access rights to prevent data breaches during each stage of the development process, have your staff sign NDA agreements and use corporate hardware on your company premises.
As of today, many financial companies undergo ISO 27001 Certification for high-security standards. The process of certification and, further, of confirming the certificate, is complex but will signify that your company uses top-notch security practices.
7. Ensure API security.
Most users run FinTech apps on mobile devices, and mobile apps use application programming interfaces (APIs) to interact with the application backend. Hence, APIs are also regular attack targets, so ensuring their security is critical for building a truly safe FinTech app.
This is typically ensured by introducing automatic API token rotation and providing identification, authentication, and authorization for accessing API.
8. Set up identification, authentication and authorization system.
The identification, authentication, and authorization system should serve as a strong barrier to any intrusion or suspicious activity. Your authentication methods shouldn’t be reduced to passwords only. Combine these methods with SMS verification or one of the most recent verification methods like thumbnail or retina scan.
At an authorization level, the app identifies the user as the one permitted to perform certain tasks or not. Ideally, user rights should be reduced to a limited set of actions and commands.
9. Use data encryption techniques.
If you operate under US legislation, it’s a must to use data encryption for users’ personal data (name, address, social security number). Financial data like credit card number and payment history, and any other info which can be received during receiving a certain financial service.
Encryption is necessary to protect data during transmission, a phase when it’s highly vulnerable and can be easily intercepted. Secure data transmission involves using various encryption algorithms; for example, the US Federal Government uses AES, which is currently believed to be the safest one.
10. Introduce the payment blocking feature.
One of the means to prevent fraud is to indicate suspicious activity. Use something that would differ significantly from the user’s normal actions, such as, for example, untypically large amounts of money transferred from unusual locations.
To protect the user from potential fraud, implement a payment blocking feature in your app. This feature will ensure payment blocking immediately, after anything that falls out of the scope of a user’s regular activity takes place.
Final Thoughts
As you can see, FinTech app security testing is a complex process requiring very specific knowledge and skills. Since FinTech organizations deal with highly sensitive data, they possibly can neither avoid or simplify the quality assurance process.
Moreover, in countries like the United States, FinTech companies have no choice but to comply with security standards imposed by federal legislation. These are the main reasons why financial institutions seek to hire FinTech QA talent, and the demand for such specialists currently outstrips the supply.
If you can’t afford to hire enough FinTech testers and QA experts to test your product at each stage of development. Use QA staff augmentation which will allow you to integrate your offshore QA talent with the in-house dev team. You’ll have cost savings as a result of access to lower-cost yet talent-rich locations.
One way or the other, ensuring top-notch security testing is an investment into both application quality and your reputation of a trustworthy FinTech company.