TikTok, a mobile video-sharing service owned by Beijing-based technology company ByteDance, has been around since 2016. Its popularity shifted into hyper-drive over the past two years, with the user count exceeding 2 billion (according to Craig Chapple, a mobile insights strategist) globally at the time of this publication.
TikTok generated a whopping 315 million installs in Q1 2020 alone, which eclipses any other app’s achievements in terms of quarterly growth.
It’s common knowledge that cybercriminals follow the trends.
Cybercriminals are following the trends — so they treat the hype around TikTok as an opportunity to extend their reach. Haters, spammers, con artists, and malware distributors can weaponize hacked accounts in a snap. Therefore, it’s in every user’s interest to ascertain that their video blogging experience isn’t vulnerable to exploitation.
The good news is, you can benefit from TikTok’s built-in security and privacy features to raise the bar for malicious actors. This article provides simple steps to harden the defenses and make your account a hard nut to crack. Before delving into the protection facet of the matter, though, let’s see what security concerns about this service have been unearthed to date.
Known TikTok Security Loopholes
In early January 2020, experts at cybersecurity company Check Point Research discovered a series of TikTok vulnerabilities that might undermine the protection of one’s account. According to the white hats, a hypothetical attacker could take advantage of these flaws to do the following:
- Compromise an account and alter its content
- Erase videos
- Upload new videos
- Change the status of private videos to “public”
- Obtain the victim’s email address and other sensitive information related to the account
SMS link spoofing is one of the malicious techniques piggybacking on TikTok imperfections. It can cause a great deal of harm with very little effort. This foul play is fueled by a somewhat crude implementation of a feature called “Text yourself a link to download TikTok,” which is available through the platform’s official website.
(Image by Check Point Research, “Tik or Tok? Is TikTok secure enough?” article)
A malefactor can use a proxy tool to skew the underlying HTTP query that consists of a user’s phone number and the legitimate app download link. This interference allows the hacker to substitute the URL with a custom value and thereby send malware-riddled text messages on behalf of TikTok.
Malware distribution and scams are the obvious use cases of this technique. The resulting sketchy site can be a credential phishing page or have exploits onboard.
Offensive mechanisms such as cross-site request forgery (CSRF) or cross-site scripting (XSS) may also kick in to execute malicious JavaScript code surreptitiously. This abuse can entail particularly disruptive outcomes, making it easy for an adversary to tamper with the victim’s browser cookies and perform different actions in their name.
What does the cybercriminal do next?
This access can pave the crook’s way towards removing arbitrary videos, adding new ones, approving followers, and making private content public. The info-stealing facet of this exploitation puts the victim’s sensitive data at risk, including their email address, payment details, and birth date. Thankfully, the company behind TikTok has since released patches for these issues.
Another pitfall is that the service isn’t too fair and square when it comes to users’ privacy.
In March 2020, security researchers exposed more than 50 iOS and iPadOS applications that regularly read the clipboard information. TikTok ended up on that list, too.
Whereas it’s not entirely clear what the application does with this data, such activity resembles eavesdropping at its worst. An additional concern is that an attacker who succeeds in compromising the TikTok app will be able to keep a record of everything the user copies to the device’s clipboard, including credit card details and login credentials for other services.
A malefactor with advanced tech skills can broaden the attack surface.
For instance, a feature called Universal Clipboard plays into crooks’ hands in this regard. It is intended to facilitate the process of copying and pasting between different devices under Apple’s umbrella.
Therefore, if an attacker takes over a TikTok account used on an iOS or iPadOS gadget, they may be able to access sensitive information on a related Mac computer.
For the record, the latest version of TikTok is no longer peeking into clipboard data. However, the aftertaste of past foul play remains. All of the reported caveats have called forth some restrictive moves at the level of governments and military branch departments.
In December 2019, the U.S. Navy banned personnel from using this service, and so did the U.S. Army shortly afterward.
TikTok Account Security Tips
Because a TikTok account is a goldmine of the user’s sensitive information, cybercriminals are lured to find ways to circumvent its defenses and get in. The following red flags may indicate a compromise and should urge you to take immediate action:
- Your TikTok password, security email address, or phone number tied to the account has been changed.
- Your username or nickname has been modified.
- Someone is removing or adding videos behind your back.
- Messages are being sent without your permission.
This brings us to the techniques that will keep perpetrators from gaining unauthorized access to your account. Below is a summary of TikTok security best practices:
1. Use a Strong Password
No matter how vanilla this recommendation may sound, it’s the stronghold of your account’s intactness. In addition to making your password at least 12 characters long, include special characters (%, $, &, etc.), uppercase letters, and numerals.
Also, make sure it looks as random as possible to prevent crooks from guessing it based on your personal details available on publicly accessible resources such as social networks.
2. Refrain from Reusing Passwords
Data breaches happen, so you don’t want your authentication info for another account to match the TikTok password. Using the same password across different services is a classic instance of a potential single point of failure (SPOF).
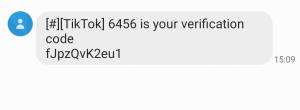
3. “Log In with Verification” Feature Can Make Your Day
If you enable the verification by adding your phone number to the profile details, the TikTok platform will be creating a one-time password (OTP) every time you sign in. But note the issue above with your phone number.
As opposed to the better-known two-factor authentication (2FA), the phone technique replaces password protection rather than boosting its efficiency. By the way, the video blogging service under scrutiny doesn’t currently provide 2FA.
A text message with TikTok verification code inside
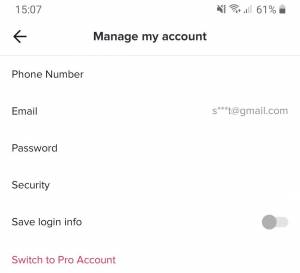
4. Prevent Your Password from Being Automatically Saved
It goes without saying that password saving is a handy option. In fact, TikTok does it by default.
The whole convenience, though, can be overshadowed by the security risks stemming from this mechanism.
Consider turning the auto password save OFF to err on the side of caution.
- Tap the Me icon at the bottom right of TikTok main screen.
- Head to Settings and privacy
- Select Manage my account
- Then slide the Save login info toggle to the left — that turns it OFF.
Switch OFF the Save login info option
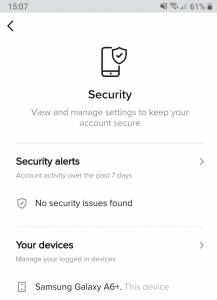
5. Stay Abreast of Account Usage Statistics
The app’s Your Devices pane lets you know what devices your account is opened on your mobile at any given time.
You may have previously signed in from somebody else’s gadget and forgot to exit the account. This is a benign scenario, though.
If the list includes a smartphone you can’t identify, it might be a heads-up. To make sure you are in the clear, go to Manage my Account, proceed to Security, and take a look at the account activity stats and the list of logged-in devices.
TikTok account activity stats
6. Stay Away from Sketchy Links
Cybercriminals may try to social-engineer you into tapping a hyperlink that leads to a malicious web page hosting a harmful payload. These links may arrive via booby-trapped text messages, phishing emails sent by strangers, or malicious redirects caused by malware.
As one of the abuse techniques demonstrates — the messages can as well impersonate TikTok. Don’t be gullible and ignore them.
7. Think What You Share
Don’t spill any personally identifiable information (PII) such as the email address or phone number in video descriptions. A seasoned hacker may mishandle the info to compromise your account.
What to Do If Your TikTok Account Has Been Hacked?
If you spot the slightest sign of a breach, go ahead and change your account password without a second thought.
Here’s how you do it: go to Settings and privacy — proceed to Manage my account, and follow the on-screen prompts to complete the procedure. As part of the attack remediation, be sure to check the accuracy of your account information on the same screen.
In case you are having issues with this, go to the Report a problem subsection under Support to access the Feedback and help screen. Then, tap the paper sheet icon in the top right corner to submit a support ticket describing your situation in detail.
TikTok Feedback and help section
All in all, TikTok is a great service bringing so many bells and whistles to your fingertips and allowing you to express yourself via nifty videos.
It’s not perfect in terms of security, though. Do your homework and tweak some settings to prevent your account from being low-hanging fruit for a cyberattack. Stay safe.