Remote working has undoubtedly helped us sail through the pandemic by following the necessary protocol of social distancing, but with this increased independence comes an increased need for security. The absence of foolproof Cybersecurity measures at the employee’s remote workplace poses a serious threat to information security and shared data over unsecured networks.
Cybersecurity Tips for Remote Workers
Some remote workers may have to use personal devices and networks for office work, and these devices might not be as well equipped with appropriate security tools that are part of any office network or system.
This makes remote working security risks increase multifold. Furthermore, any data leakage can incur severe costs to organizations. Hence, it becomes essential for employers to have a robust cybersecurity plan for their remote workers.
Here are some simple hacks to ensure that you, your remote working employees, and the company are not put at risk of data theft or email hacking.
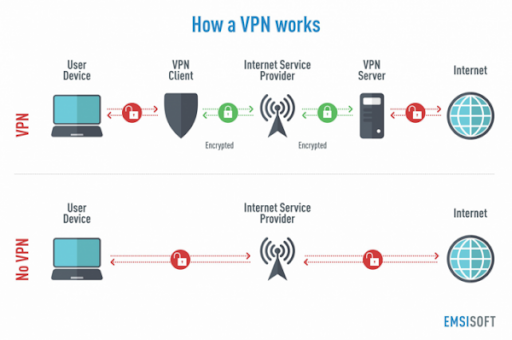
Enhance Your Cybersecurity by Using VPN
Use of VPN is a must when operating from any public Wi-Fi network. These are unsecured networks with no firewalling between various users; they make you more vulnerable to falling prey to hacking attempts. VPN or Virtual Private Network is a private connection that accesses the internet through a “third-party” server instead of directly connected to the targeted network.
VPN provides secure, encrypted connections between the remote work location and headquarters using encrypted tunneling protocols supported by operating systems and devices.
It thus, hides your online identity and your activities on the internet, protecting against any malicious attempts by hackers.
Hence, a VPN is the perfect solution for organizations looking for an economical way to protect their data when they are on the go, or their employees are away from corporate networks by keeping remote employees’ access masked from hackers.
Another critical point to remember as part of remote work security best practice is protecting your home Wi-Fi network by turning on the WPA2 encryption and choosing a strong password.
Pay Attention to Use Of Strong Passwords
Work towards creating stronger passwords and better passwords in general. For example, choose a long password with an arbitrary mix of upper and lowercase letters, special characters, and numbers.
Anything less is open to brute force attacks and can be easily hacked with a dictionary attack. More is always better! And don’t use the same password for multiple accounts (e.g., your bank username and your online retailer username).
Another way to ensure password security is to use a management tool like LastPass or KeePass. These technologies will generate and store your passwords, so you only have to remember one master password for authentication. The best thing about these tools is that they are cross-platform so that you can use the same tool on Windows, Mac OS X, Android, iOS, and even Linux.
An extra layer of security can be added to your accounts by using two-factor authentication, which involves a two-step verification of username or a password. The second step requires verification using code sent to you through email or phone messages.
Choose SSL Encryption
An SSL or Secure Socket Layer Certificate encrypts all the communication between the user browser and the web hosting server. Secure Socket Layer (SSL) protects the crucial user data from being stolen by hackers. A standard attack is called: Man-In-The-Middle attack.
The SSL secured website uses secured protocol HTTPS, ensuring safety for data exchanged between your web browser and any website you might be visiting.
You can buy a cost-effective, cheap SSL certificate to secure your portal from an array of choices available with many reputed SSL Certificate providers that suit your budget and security needs.
We can suggest you RapidSSL authority that offers single domain and wildcard SSL certificates that are available at a low price. You can buy RapidSSL Wildcard SSL for a single domain and multiple subdomains respectively.
Have A Web Application Firewall Security
A firewall blocks any malicious code from entering your system at the very entry point. It essentially forms the very first protective layer against any malware attack. It helps ward off any data breach or crucial organization information leaking from the remote worker’s device.
Ensure that the in-built firewalls of your operating system and router are enabled to provide security to your device.
Using a web application firewall (WAF), a software application that monitors network traffic on an organization’s internal or external networks, will protect the organization’s applications against unauthorized users accessing or altering data.
Focus On Remote Employee Training
Pay attention to training your remote workforce to follow the best cybersecurity practices. Apart from setting up appropriate security tools for employees, proper training is the other method to keep your information safe. By understanding the threats that could leak your organization’s data, employees will be able to protect data while working remotely.
Secure Your Systems with Regular Updating and Backups
Updating your system should occupy the topmost priority in your security policy. For example, if remote employees use an outdated operating system, several files and programs could be at risk. Therefore, ensuring that their system has the most recent updates installed is essential.
Make sure your devices are patched. Update your antivirus software regularly. Install antivirus on mobile devices, use security controls such as encryption on removable media on laptops and email and documents on shared drives. Ensure that all your devices, including laptops, desktops, tablets, etc. have the latest patch installed.
Back up your data regularly, manually, or you can use automated data backups. It will minimize your downtime and help you restore your systems in case of any cyberattack.
Be Wary of Phishing
You should always be alert and be aware of phishing attacks by hackers. Emails, text messages, or even instant messages can be used to send phishing links or attachments; never click on them.
These emails seem to carry emergency messages from trusted sources like your organization or might be personal and would try to persuade you to click a malicious link or share crucial login credentials. As part of a remote working team, you should remove such emails and convey them to your IT department.
Conclusion
In conclusion, we can say that you must make your remote work secure by adopting these simple yet very effective cybersecurity tips and working on a hardened security policy for your organization.
Therefore, set proper controls and procedures to ensure that it includes all the above-discussed pointers so that your company’s sensitive data will not be compromised.
Employees at all levels should be motivated to follow these standards and best practices to protect against cyber-attacks.
Image Credit: Provided by the Author; Thank you!