By now, most folks have heard of phishing scams, and know to be on the lookout for fake PayPal and bank sign-ons. But what happens when your co-workers get a link to a site that looks just like the corporate intranet? Using the Simple Phishing Toolkit (SPT) you can find out.
The concept behind SPT is pretty simple: Most companies spend a fair amount of money on trying to secure their environment. How much do they spend on educating users? Very little, and in many cases nothing at all. As the saying goes, an ounce of prevention is much better than a pound of cure.
Working with SPT
Basically, SPT is a PHP/MySQL package that is designed to create and run phishing campaigns. It should install on any current LAMP or WAMP stack in just a few minutes. If you’ve installed Drupal or WordPress or any other PHP/MySQL package, it shouldn’t take more than a coffee break to set up. (Creating the database and MySQL user is the longest part of the process.)
From there, you can create campaigns to try to “hook” users and see if they’re gullible enough to hand out credentials to a phishing site. You supply templates to SPT for the target site, and the list of users and the body of the email. It will send out the phishing emails and collect data when users respond.
Note that there are two ways to provide a template to SPT – provide a template that you’ve created, or scrape another site. In my tests of SPT, the scraping didn’t work. You can find a Microsoft Outlook Web template on the SPT site, though. This might get you started right away if your organization uses Outlook.
You can also provide an “education package” so that users get schooled as soon as they fall for the phishing link. This can be triggered as soon as users click on the link, or after they provide data.
Could be Used for Good or Evil
The project is open source, available under the GPLv3. It’s also extensible, so if it doesn’t do everything you want there is the option of writing modules for it. The project is still relatively young, I tested the 0.4 release. Now might be a good time for IT departments to talk to their users about phishing, then plan a SPT campaign for later in the year.
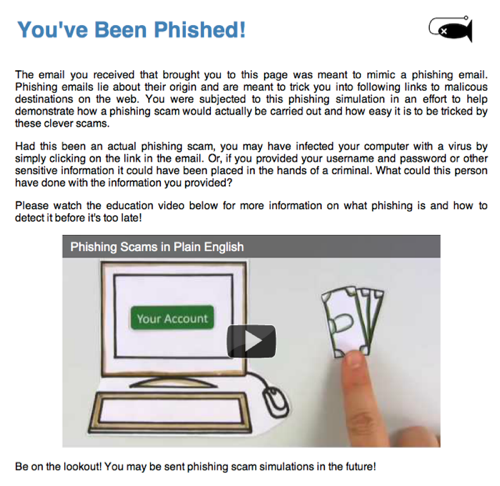
It’s worth noting that SPT could be used to run actual phishing campaigns, but those are going on already anyway. Yes, SPT promises to be a really easy way to set up a phishing attack, but that’s all the more reason to start educating users.
Does SPT look like something you’d use in your business? Are you doing anything to educate users about phishing already? Would love to hear more ideas in the comments about educating users rather than just spending money on security measures.
Hat tip to Krebs on Security, where I learned about SPT.






