On September 14, 2009 New York Times readers were automatically redirected to a site hosting malmare thanks to an ad containing malicious code. On July 15 2010, TweetMeme was the victim of a similar attack and began sending its users to a “scareware” site. These are just two examples of “malvertising,” one of the fastest growing security threats on the web. It’s particularly scary because potentially any site with advertising could be a target, and users don’t even have to click the ads to trigger malware. Use a Mac? You could still fall victim to phishing scams perpetuated by malvertisers. Scary stuff. So what do you need to know?

Malware Isn’t Just on “Sketchy” Sites Anymore
In the past, users who didn’t frequent adult, gambling or other “sketchy” sites were relatively safe from harm. Now any site that contains third party content – even your own company’s web site – is at risk. Earlier this year, Dasient released a report identifying the top three security vulnerabilities enterprise web sites contain: advertising was one of the three, along with other third party content.
According to ClickFacts CEO Michael Caruso, malware scammers are increasingly moving away from e-mail and buying advertising instead. An ad on a popular site can reach millions, and automated ad purchasing makes it easy to criminals to buy ads. According to Caruso, malvertisers will sometimes walk into offices impersonating legitimate buyers when automated systems aren’t available, and often pay for ads with fake or stolen credit cards.
Malicous advertisements on search engine sponsored results and even organic search results is an increasing problem as well. Here’s an example of a sponsored search result found on GoogleBing by StopMalvertising.com:
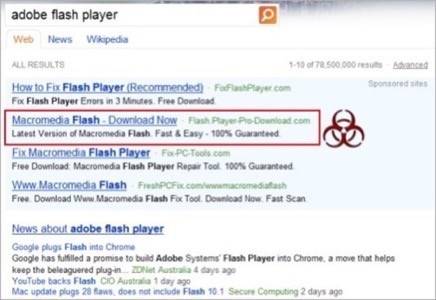
Users who click the above ad are taken to a fake Adobe Flash web site where they are encouraged to download a malicious app.
Curaso also notes that it’s become extremely easy for criminals with little technical proficiency to conduct malware campaigns as exploit kits are sold on the open market from servers in places like eastern Europe and China.
Users Don’t Even Have to Click the Ads to Get Infected
According to Chris Larsen, head of Blue Coat‘s research lab, you don’t even need to actually click on the ads. Blue Coat documented one way this is done: a site can use JavaScript to call hidden iFrames which load PDFs containing code that exploits Adobe Reader vulnerabilities.
Non-Windows Users Can Also be Affected
Non-Windows users can also be targeted by malvertising via phishing scams, though they will generally have to click on the ads served. Caruso told us about an instance of malvertising in which scammers bought ads that appeared to be from a major bank. Once users clicked through to the landing page, they collected bank account information from victims.
Malware has Graduated from Nuisance to Serious Threat
Larsen says that in the past there were two type of IT threats. First, mass non-targeted attacks that force or trick users into downloading malware. These have traditionally been mere nuisances for IT to deal with, as the symptoms (fake AV notifications, pop-ups, etc.) become rapidly apparent. Second, highly targeted attacks which perpetrators may spend months researching. These are more dangerous because the perpetrators are looking for specific, valuable company information.
The emergence of botnets has made malware into a serious threat. Compromised machines may not show any signs of infection, leaving backdoors wide open for exploitation. Larsen says it’s been suggested that since botnet operators sell their services on the black market, those attempting to target a specific company could approach botnets with a list of IP ranges and offer to purchase control of specific machines in order to get a foothold in a specific network.
Patching will Protect You
Here’s the good news: according to Larsen, most malvertising targets well known exploits. Keeping your operating systems and software patched is the best way to prevent damage from attacks.
Patch management is a notoriously labor intensive and thankless process, but as NSS Labs recently noted in a report it’s one of the most important steps IT can take to protect its users.
Who’s Trying to Help?
ClickFacts and Dasient both offer services to scan ad networks for malicious advertising. Dasient recently landed the ad network AdOn as a client, and ClickFacts counts News Corp as a customer. Last year, Google launchedanti-malvertising.com (not to be confused with StopMalvertising.com) to help ad networks identify malvertisers.
One stumbling block security companies face, according to Larsen, is that ad networks tend to be secretive about how they serve ads in order to circumvent ad blockers. When ad networks aren’t forth coming, it can be difficult to determine how malware is being served up and how to block it.
Caruso points out that companies shouldn’t be placing blame – instead ad networks, publishers and security companies need to work together to solve the problem.










