
The conventional wisdom holds that your organization will be secure if you focus on shutting down zero-day exploits and keep out the rest of the exploits by applying multi-layer defenses from multiple vendors. That complacency is about to take a serious beating from new research coming out of NSS Labs this week.
The news really could not have come at a worse time. Last week’s revelations that China may be participating in state-sponsored cyberattacks against Western nations, coupled with Anonymous’ full-on declaration of war against various corporate and government agencies following the death of Aaron Swartz, mean that security is very much on the minds of IT leaders these days. Finding out your bulletproof vest is made out of cardboard instead of Kevlar just as the firefight is heating up does not make for happy security executives.
Bypassing The Kill Chain
Good news or not, Frank Artes, Research Director at NSS Labs, are spreading the word about the research he and colleague Stefan Frei have done.
After analyzing the massive amount of data NSS Labs collects as it analyzes security products up and down an organization’s security stack (known as the kill chain), the team discovered that the usual practice of using heterogeneous, layered tools to filter out exploits is not as effective as one would think.
The idea of this layered approach, Artes explained, is based on the premise that even if an exploit can get through one vendor’s defenses, another vendor’s tool can catch that exploit and kill it. Hence, “kill chain.”
But in reality, “huge numbers of exploits are getting through,” Artes said. The NSS Labs researchers mapped those exploits and identified them based on criticality and availability (is the exploit hard to get or part of a crimeware package that a script kiddie can buy with a credit card?). Using a visual model, the team was able to create graphic results that demonstrate just how many serious exploits can get through.
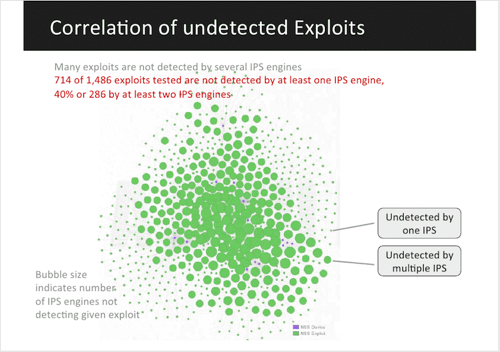
Exploits Don’t Have Expiration Dates
NSS Labs, which acts as a Consumer Reports-like organization in the security sector, is not singling out any one vendor as a problem. Instead, Artes emphasized, all vendors’ products, be they browsers, Intrusion Prevention Systems (IPS) or firewalls, have exploits that can let malware through, and a surprisingly high number of these holes are shared among various products.
Part of the problem is that many vendors are so focused on security in the present, such as protecting customers from zero-day exploits and advanced persistent threats (APTs), such as state-sponsored attacks.
“We’re always looking forward, watching out for the next Duqu or ILoveYou for 2013,” Artes said. What should also be done is keep an eye on what’s happened in the past, because it can come back to haunt you.
Exploits don’t have expiration dates and there are a lot of older methods and tools that can bust through security because the security software may never have been properly patched or (in some cases) the exploit may have been deprecated from the security tool’s database to make room for newer exploits. Databases for security software can’t afford to get too big, Artes explained, or their tool’s performance would be hindered.
End users patch-management policies can also affect how many exploits get through. Because many applications can touch parts of a security stack, you can’t just automatically update every single piece of security software to the latest and greatest – without extensive testing, business applications could break and die when confronted with freshly patched security code.
Revisiting your company’s patch-management procedures is a good way to help ensure systems are locked down as much as possible. Devoting more resources to these procedures is your best bet, Artes explained, but many companies don’t have the time or the money to beef up patch management.
Instead, they may have to work smarter, not harder. Tools like the visual analysis Artes and Frei’s team have developed should help focus efforts, even on a fixed budget.
Lead image courtesy of Shutterstock.
















