Back in the 1990s, U.S. government agencies were officially transitioning their identity systems to smartcards. The Homeland Security Dept. did not exist yet. So the agency expected to lead the way was the Defense Dept., which had a Common Access Card initiative, but not really enough fuel to keep that initiative going.

After Sept. 11, 2001, the new DHS department was ordered to carry out Homeland Security Presidential Directive 12 (HSPD-12) – an order mandating a smarter card that contains its own biometrics, effectively invalidating the card if someone else happens to be holding it. It’s a decade later, and agencies throughout the government are moving to cloud architectures. Now DHS is taking step 2 in the rollout of a defense identity management system (DEFIMNET) forged through trials with DOD. The challenge, as the CEO of the manufacturer of this system tells ReadWriteWeb, will be to live up to HSPD-12 expectations that were written before the cloud as we know it today was even conceived.
Swipe This
“We are providing a system that allows a government worker or contractor to access data outside the fortress, for lack of a better term,” states Route1 CEO Tony Busseri in an interview with RWW. Painting a picture of something looking quite the opposite of a cloud, Busseri describes a system that incorporates Route1’s MobiKEY Fusion device, which enables access to this fortress from remote devices by way of a smarter personal identity verification (PIV) card.
“We often get lulled into a comfort level in today’s marketplace where, if you put the right password into the right computer or tablet with the right software on it, that means we’re doing a good job of authenticating the individual. It doesn’t. What it means is that you’ve authenticated an asset.” Meaning, there’s no guarantee that the thing that delivered the password is a person as opposed to a resource acting on the person’s behalf. The latter may be a convenience for some private enterprises. But it fails to meet the specifications of HSPD-12.
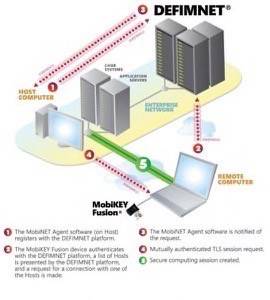
Contrary to some of the designs and aspirations of cloud architectures, sensitive government data should never extend outside the fortress boundaries depicted in the diagram above, asserts Busseri. “Specifically, data should not go outside these entities’ firewalls. Too often in today’s world, we believe that to support teleworking or mobile computing, data has to go with you on the device that goes outside the network. We’re bombarded by messages from folks that deliver an Android or iOS-based operating system – everyone talks about how as data gets bigger, it’s going to create a better experience for the worker. We fundamentally believe that the greatest security risk is when data goes outside the firewall. The administrator, or whoever you want to identify as the lead, no longer has eyeballs on that information. There’s no way of ensuring it will ever properly, completely come back inside the network.”
The Argument for Keeping the Fortress From the Cloud
One argument we’ve heard from cloud and virtualization solution providers is that secure, remote access through virtual sessions enables workers to fully access resources from within what Route1’s Busseri calls the “fortress,” without actually having to move data outside that fortress and copy it to local storage on remote devices. Done properly, they say, remote virtual access can be at least as secure as on-premise access, if not more so.
Busseri disagrees. “There’s no way data should be going up into a cloud, from my perspective. It should be staying behind the firewalls, within the fortress, within the network,” he remarks. Although his company’s principal clients are government agencies, Busseri is on the record as against language in the Senate’s 2011 cybersecurity bill that would grant a federal authority the right to take control of private systems housing government data, such as cloud service providers, in the event of a national cyber-emergency. If the system is designed properly, he says, the fortress need not extend its boundaries when times get tough.
“We make a big leap of faith to say that, in a moment of crisis as defined by our politicians and our leaders, they can take control of our systems. It assumes that those who are in control actually have great security. If that [plan] were implemented today, it would be a mess… If we allowed them to take control of networks and information and data, it would likely become even more vulnerable as a result of that control. So until the federal government gets as secure as it can be today, I don’t know why we would ever implement this.”
















