Tim Greene, writing this week in Network World, brings up the latest developments in improving SSL certificates. As many of you recall, earlier this year we had two big security breaches involving these certs, including a situation where Comodo issued and then revoked a series of nine fake certificates. While the fakes weren’t actually used, it was a close enough call.

The problem is that your browser has a hard-coded list of certificate authorities (CAs).
If you haven’t ever been to this part of your browser settings, you can bring it up now (Firefox is Tools/Options/Advanced, Chrome is Tools/Options/Under the Hood, etc.) and see a long list of CAs, some from companies that you may recognize (Microsoft, Thawte, Verisign) and many from companies that you probably have never heard of. (How many of us had ever heard of Comodo before the cert hack reported earlier this year? My point exactly.)
Every time you go to a site using https:, it checks in with these CAs to determine if the cert from the destination website is legit or not. Most of the current browser versions will report on the identity of the website in the address bar and whether or not it checks out. If you go to PayPal.com, for example, it automatically redirects you to https: and you can click on the notification to see the cert as shown here:
To combat the bad guys, many more sites are now using SSL protocols: Gmail now defaults to it for reading your emails, for one notable example. But all this security infrastructure goes out the window if the certs can’t be trusted.
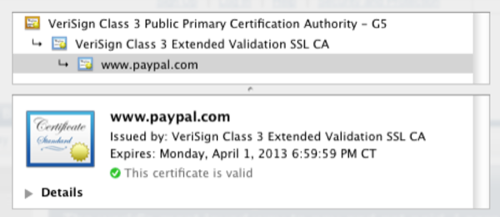
Getting a cert is easy: it just costs money (here is one place you can comparison shop for them) and even your friendly registrar can quickly provide one. You can also self-sign your website with your own cert, which will bring up a warning in most modern browsers for your visitors. When you purchase a cert, a chain of trust is established between the CA and your website using the cert, as you can see in the PayPal example above.
But what if this circle of trust is compromised, as the character played so brilliantly by Robert DeNiro asks in the “Focker” films? That is why we need an Internet SSL notary public for SSL certs. Unlike the notaries that we all use from time to time for our paperwork, the process would involve a crowdsourced collection of certs that people already have trusted, rather than a single entity that would vet the certs from on high.
And this being the Internet, of course there are two different proposed notary standards, called Perspectives, from a team at Carnegie Mellon, and Convergence from an independent test lab. They both make use of Firefox plug-ins, and both are relatively new and unused by the vast majority of sites and the browsing public. The idea is just like picking which search engine site you will use by default, you can also choose which collect of notaries to trust for your SSL certs.
Whether these notary efforts will catch on isn’t a sure bet: indeed, they have to be widely deployed before they are truly useful, and support more than just Firefox browsers too. But we definitely are overdue for better SSL root CA infrastructure, otherwise we will suffer the same fate as Ben Stiller’s character.

















