For large software development teams, Microsoft Visual Studio has one feature whose functionality actually resembles that of Outlook in one regard: The addition of workflow templates gives team members manageable lists of tasks to be done. The Security Development Lifecycle (SDL) is a set of best practices originally developed by Microsoft for Microsoft, to compel its own engineers to start incorporating better security practices as far back as the architecture stage.

On Wednesday, the company initiated public support of its SDL template in the tool that most Windows developers use today (at least, those who aren’t using the VS2012 beta): Visual Studio 2010. Along with that support comes the latest revision to the company’s threat modeling tool, and some new “things to do” for the list: two fuzzing tools designed to take down insecure apps. These tools help developers spot potential vulnerabilities in their code.
Anybody who’s watched a demo from one of Microsoft’s security developers has probably seen MiniFuzz, an automated tool designed to do a little mischief with applications you’re building. Whenever your application uses a type of file, MiniFuzz attempts various contortions of that file to see if it can trigger a stack overflow, or some kind of vulnerability that can be exploited. It’s not new at all, and in fact, developers have been using it with Visual Studio 2010… but apparently not all that well, particularly with respect to Team Foundation Server 2010. MiniFuzz did support TFS 2007, and developers have jerry-rigged it to use TFS 2010.
Today, Microsoft confirmed to RWW that they no longer have to jerry-rig it; support for TFS 2010 is built in. RegEgFuzz was also updated; it’s a tool that “fuzzes” regular expressions that a program may parse, to see if it can trigger a vulnerability there.
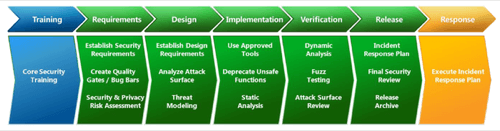
The actual Security Development Lifecycle itself is a seven-stage process, the middle five of which (shown above in green) can be automated through best practices agendas. These agendas are represented by the new set of templates available for Team Foundation Server 2010.
In Microsoft’s annual progress report for the SDL produced last March, the company cited reports submitted to the National Vulnerability Database in 2010 as an indicator of the platform’s success. Surprisingly (though Microsoft didn’t exactly spotlight this), reported vulnerabilities in Microsoft-branded products rose slightly last year, after several declines.
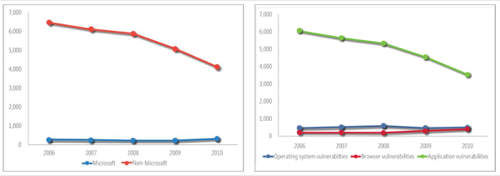
The incline looks a little better when paired on the same chart with the ongoing decline in vulnerability reports for non-Windows apps (on the left), which has declined significantly. The chart on the right shows operating system-related vulnerabilities are more to blame this year than in years past, which is a slight step backwards for Windows 7.
The report also reads, “In January of 2011, Forrester published the results of a Microsoft-sponsored survey of top software development influencers across North America. Forrester found that, though application security was not a mature practice for many, those employing a coordinated, prescriptive approach experienced a stronger return on investment.”

















