Currently, we consider ourselves lucky if we don’t get stuck in traffic while driving to the office. The struggle of even finding a parking spot for your car is real. The smart city industry is projected to reach the $400 billion mark by 2020. The urban population is increasing at an alarming rate. According to one survey, 65% of the world’s population will live in cities by 2040. It sounds like chaos to me. We will need cybersecurity to ensure the sanity in smart cities.
In today’s world of digitalization, the world is already familiar with the concept of IoT, AI, and Robotics. Using these latest advancements to our advantage, we can prepare and self-equip our cities to support the increasing urban population.
Currently, only 600 urban cities contribute to 60% of global GDP. The idea of a smart city is to collect information through connected devices and make life more comfortable using these devices for logistics. If we follow the promising results of smart cities, every drive to your office will be a lucky one! You will know exactly where to park your car every time you reach a shopping mall or a supermarket. Sounds perfect.
Cybersecurity in Smart Cities – The Problem Statement
In 2012, a Puerto Rico electric utility company asked the FBI’s help after its smart meters got hacked and reprogrammed. When the company was reprogrammed, it allowed many people to pay substantially lower electricity bills. Smart meters had been introduced by the company to improve the efficiency and comfort of its consumers.
Multiple such cases have been reported over the years concerning the increased vulnerabilities of smart devices against cyber threats.
Without ensuring proper security measures, the risk of cyber threats can make one’s life more costly, dangerous, and painful in a smart city. There are many aspects of cyber securing a smart city, including the role of connected devices, isolating vulnerabilities, establishing secure endpoints, and dealing with evolving threats.
Identifying Vulnerabilities – What determines the security of Smart Cities?
Everything is connected in a smart city.
Having everything connected opens up the possibility of multiple pain points in a single infrastructure. Even a single vulnerable endpoint can corrupt the entire infrastructure allowing data theft, device hijacking, Distributed Denial of Service (DDoS), and more.
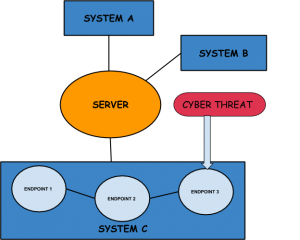
To give you a better idea. Let’s say that there are three systems – A, B, and C connected to a single server in an infrastructure. If an attacker finds a security flaw in Endpoint three of System C, they have entered and can end up corrupting all the connected endpoints and systems of the entire infrastructure.
The server of any smart city infrastructure is designed to help consumers and has user-centric information. It could be anything from trivial data – names and addresses to confidential information.
Confidential information includes bank account details, IP addresses, and other information.
Though the significance of data you share in a smart city infrastructure might not seem important to you, but the information is a blessing for a hacking entity. A hacker loves knowledge.
As such, the first step towards a secure smart city is identifying vulnerabilities and possible entry points for hackers in each infrastructure. It could be a single, smart meter in an extensive power grid system.
Remember how we were talking about hitting just green lights on the way to our offices. Imagine the chaos in a smart city with thousands of vehicles on the road if someone hacks into the traffic infrastructure and turns every light to green.
The Role of Connected Devices
By 2025, there will be over 21 billion connected IoT devices, says US Norton, an internet security company. When we are talking about sensors, smart infrastructure, smart electricity, and smart data, what ties them all together? The answer is the Internet of Things.
Remember, not long ago, everyone was talking about smart homes and how your smartphone can control the functioning of everything in it? Well, a smart city is like implementing the technology of smart homes in the entire city.
You may be wondering why you should put your confidential data at stake? The most straightforward answer is that without the Internet of Things, connected devices, or shared information, the concept of a smart city would remain a dream.
It’s the data and the shared devices that make the whole system work. In smart cities, everything is inter-webbed, and the attack surface and possible weak links increase multi-fold for a hacker.
Connected devices – be it smart sensors, your mobile phones, smart meters, or anything else, are the only source to derive information that is used to enhance user experience or quality of life in a smart city. The deployment of connected devices across public domains is mandatory to establish interconnectivity in smart cities.
So, where do you begin your journey if you want to cyber-secure a smart city?
Security of a Smart City: Where to Begin?
The entire concept of smart cities is comparatively new, and one of the many challenges faced in cyber-securing a smart city is the lack of anticipated intelligence.
How do you ensure the security of such a vast network area?
Start at the bottom and move up from there – one step at a time. While governments are finding it hard to implement the essential internet privacy and security rules, many countries are starting to realize the significance of implementing cybersecurity regulations in their smart cities.
For instance, the GDPR was formulated by the European Union to safeguard the data privacy of all individual citizens of the EU and the European Economic Area (EEA).
Certain steps can be implemented to ensure data security and privacy in smart cities.
The management of smart cities needs to define clear boundaries for protecting the information and the extent of its usage right at the source. Besides these, the mobile and web applications (if any) that are responsible for the interconnectivity among IoT devices need to foolproof and created by highly experienced developers.
Against hiring full-time developers, you can hire a dedicated Laravel developer or any other developer using the Staff Augmentation model. Use wearing international boundaries to your advantage and save business dollars while ensuring the quality of your IoT services. Implementing smart city security solutions can be tricky but we have to start somewhere.
Securing Pain Points: Dealing with Evolving Threats
Every new technological discovery in today’s era can end up giving hackers a new tool or creating a new loophole to break into the inter-webbed network of our smart cities. Given that, is $135 billion enough to secure the entire web of connected devices across various sectors in all our smart cities by 2024?
Considering the number of connected devices and the complexity of the entire network in smart cities, human efforts won’t be enough for creating the required impact when dealing with evolving threats in cybersecurity.
We need security solutions that can detect evolving cyber threats and prevent them from corrupting infrastructures in smart cities.
In such a scenario, a possible feasible solution can be deploying Artificial Intelligence for cybersecurity. The AI security elements can be programmed to learn and detect any foreign elements in a smart city infrastructure.
But is AI enough?
There has been news and questions rising regarding the bias-ness of AI. Taking this into consideration, how do we deal with evolving cyberthreats in smart cities? There needs to be more research-based development of artificial intelligence in cybersecurity following well-defined legal and ethical guidelines.
Safety of Smart Cities Beyond Cybersecurity
Establishing resilience against cyber threats in smart cities is necessary. It becomes crucial to ensure that every smart city has a backup plan in case its functioning infrastructure goes down. A backup plan will ensure that critical services such as traffic networks of a smart city remain functional even if its infrastructure is under attack.
Surveys have shown that users are willing to offer more personal data when reassured of its safety.
Finally, an entity or an appointed officer needs to be accountable in case of identity theft, DDoS, PDoS, and more. The technology is evolving at an exponential rate and it’s almost time that we will live in smart cities. But, it’s high time to ask the question: Are we ready yet?


















