2018 showed us an accelerated growth in cyber threat activities. Data breaches, attacks using malicious software and insider threats were among the most familiar forms of attack.
Many well-known organizations suffered from these cybersecurity disasters and compromised data of millions of users.
Exactis, a marketing and data aggregation firm suffered the largest data leak of last year, exposed 340 million records on a publicly accessible server.
While these threats will continue to be a part of 2019, companies are going to encounter more sophisticated threats due to advances in technology like artificial intelligence, machine learning, and blockchain. Here are the top six threats that organizations need to watch out for in 2019.
-
AI-Generated phishing emails.
Human-generated phishing attacks involve digital messages to trick people into clicking on a malicious link that installs malware or exposes sensitive data. AI-generated phishing emails are way more dangerous than the ones generated by humans.
Now, Hackers are able to create highly realistic “deep fake” video and audio to fool individuals. A good example is the falsified video made by Buzzfeed which shows Jordan Peele doing a Barack Obama impersonation and calling “President Trump a total deep shit”.
Earlier, big movie studios were required to create such deep fake videos. Now anybody can create such ploy with a decent computer and a powerful graphics card.
Through DeepFake algorithm, cybercriminals can easily spread false news, stoke geopolitical tensions during the time of elections.
-
CryptoJacking.
Crypto jacking is a form of cyber attack in which the attacker hijacks third party computer, tablet, mobile phone, or connected home device to mine cryptocurrency.
Bad actors use a malicious link or infect websites or online ads with javascript code that launch the crypto mining code in the victim’s system.
A report generated by Adguard showed a 31 percent growth-rate for in-browser crypto jacking.
The reason behind crypto jacking is becoming more popular because cybercriminals can make good money with minimal effort.
In February 2018, more than half a million computing devices were hacked by a crypto mining botnet called Sominru. Proofpoint, a cybersecurity firm estimated that the operators had mined 8900 Monero close to 3.6 million in value.
Kevin Haley, director of Symantec Security said “As long as cryptocurrencies have value, attackers will use computers to steal it.
-
Attacking from the computing cloud.
Last year, the US government accused two Chinese hackers of stealing data from at least 45 U.S. tech companies, government agencies as well as the personal data of more than 100,000 members of the U.S. Navy.
The indictment said that the defendants hacked companies that remotely managed IT infrastructure of business and government around the world.
Such attacks are major threats to the companies that host other companies’ data on their servers or manage clients’ IT services remotely.
By sneaking into the system of these companies, hackers can also infiltrate the clients too.
Looking at the advancement in digital technologies, most of the companies will employ cloud solutions to host their IT infrastructure.
Companies should choose big cloud companies such as AWS and Google as they are much safer than the smaller companies which are more vigilant to these attacks.
-
Hacking blockchain smart contracts.
Blockchain is widely used in various applications because it provides transparency and security by encryption. One of the most promising use cases of Blockchain technology is smart contracts.
These are software programs running on top of blockchain which automatically processes some form of digital asset exchange if the pre-defined rules meet.
From carrying out financial transactions to intellectual-property protection, smart contracts will be vital to all such applications. While smart contracts have potential use cases, this relatively new technology still has bugs as claimed by researchers.
In 2017, a vulnerability in a multisignature technology of a digital wallet – Parity, was exploited by hackers and $32 million of digital currency was stolen. The fundamental problem associated with keeping the smart contract data private is with the inbuilt transparency of the blockchain.
Attackers have already identified this vulnerability. It will be a huge challenge for companies who will leverage smart contracts in 2019.
-
Mobile malware.
Mobile devices will be a top target for cyber threats in 2019. According to Symantec Internet Security Threat Report, new malware variants for mobile devices increased by 54% in 2017.
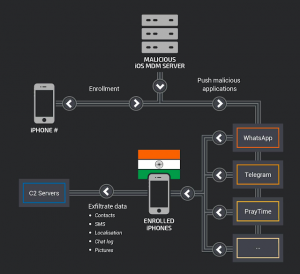
Cybercriminals are developing new ways and new tools to spy on iPhone and Android devices. Last year, security and intelligence firm Talos found that a hacking group abused mobile device management (MDM) protocol to target a few iPhones in India.
It was found that the hackers gained access to the devices through physical access and social engineering attacks to secretly spy and steal the data.
Source: Talos Intelligence
The best way to prevent mobile malware attacks is to avoid clicking on links and downloading files from unknown sources. It’s also important to have updated OS on your mobile devices as these are less likely to get affected by cyber threats.
-
Hacking AI defense with AI tools.
“Organizations know the benefits of AI technology to defend their system, but they are also aware that attackers have unique capabilities to exploit their system with that same technology,” said in a press release by Rodney Joffe, Neustar senior vice president.
A lot of cybersecurity defense firms have started to implement AI models to detect cyber threats. Unfortunately, cybercriminals can create more sophisticated attacks by infiltrating these defenses.
This can be carried out using generative adversarial networks, which involves two neutral networks contesting each other to discover the AI algorithms each is using. If the hackers discover the algorithm, they can easily develop a model to bypass it.
Another potential risk of the adversarial network is that hackers can infiltrate data sets used to train AI models – for instance, injecting malicious code and modifying labels so that threats are identified as safe rather than a suspect.