
When IT managers build a Bring Your Own Device (BYOD) plan, chip architecture usually isn’t high on their list of considerations. At first glance, it’s easy to see why. After all, processors work or they don’t – there isn’t a lot of support to be done, right?
But there’s more here than meets the eye. Thinking about the silicon that powers your supported devices can pay off big, providing better performance, security and manageability. It might even keep your legal department happy.

Simplicity First
There are plenty of exciting consumer devices to catch your employees’ eyes, each with its own combination of processor, operating system and form factor. The task of a BYOD program is not necessarily to support all of them, but to choose the devices that best match customer needs, security concerns, business demands and available resources.
New devices introduce risk and complexity to every aspect of your ecosystem, from provisioning and training to security and support. The more varied the range of devices you allow, the greater the stress on your operations. The keys to meeting your goals are platform simplicity and consistency. Choosing to minimize deviation simplifies administration and allows IT to leverage as much existing infrastructure as possible. That choice starts with the processor.
The Processor Market
Intel and ARM Holdings are the two primary competitors in the mobile chipset market. Intel’s high-performing Core-series processors power the majority of laptops, Ultrabooks and notebooks, and its low-power Atom processors are gaining market share in tablets, smartphones and hybrid devices. ARM-based chips – most commonly found in tablets and smartphones – have recently begun to appear in laptops and hybrid devices.
Intel and ARM take very different approaches to chip production. ARM licenses its designs to semiconductor manufacturers, which then fabricate their own processors based on those designs. This flexibility is attractive to hardware companies, and allows ARM-based chips to power a wide assortment of devices, from appliances to servers.
The downside of that flexibility is inconsistency among ARM-based designs. Samsung and AMD both manufacture ARM-based chips, but their processors are substantially different. Intel follows a different business model, designing and producing all of its own silicon. This approach establishes a baseline across multiple manufacturers. This consistency is the reason Intel-powered Apple MacBooks are capable of running Windows natively, for example.
Application And OS Support
Businesses run on applications, and processor choice can impact how (or whether) those applications run. The most obvious example is as basic as the operating system itself – most notably in Microsoft Windows.
When it launched Windows 8, Microsoft decided to support ARM-based chips for the first time. Windows RT, an operating system targeted at lower-cost consumer devices, like the Microsoft Surface, is the company’s first ARM-based OS.
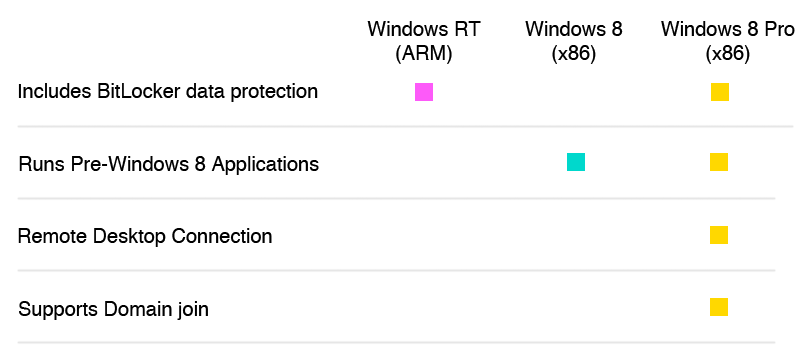
While RT shares many of the same features as Windows 8 and Windows 8 Pro, it is not fully compatible with the entire Windows ecosystem. On its website, Microsoft outlines the major differences between RT and its other operating systems. For a consumer starting from scratch, Windows RT and applications available through the Windows Store may be more than enough. For enteprise IT managers, though, the differences become more troubling.
The most significant IT concern is the lack of support for “legacy” applications. Windows RT simply cannot run applications designed for previous versions of Windows. Depending on your existing investment in Windows apps and their business necessity, this can be an annoyance – or an absolute showstopper.

Other missing features, like Remote Desktop and Domain Join, may be less essential, but still add to the support burden for RT devices and could complicate efforts to create a simple, comprehensive management solution. In an all-Intel, Windows 8 environment, IT managers can leverage time-tested, existing management applications to extend their reach without writing custom software. As soon as one RT device is added to the mix, custom coding is required.
Not all consequences of a heterogeneous environment are technical. Employee-owned devices are already notorious for violating enterprise software licenses. When classes of employee devices come stocked with different software than your other devices, your existing license agreements may not provide coverage. For example, Windows RT comes pre-loaded with Office Home & Student 2013 RT Preview. Unless a business anticipated supporting that device and took the necessary legal steps, using that program in a business setting could violate the software’s licensing provisions.
Hardware-Based Assistance
Chipsets rarely fail, for good reason. Once it’s pressed and placed into a computer, a processor is essentially untouchable by applications, the operating system, or overzealous users. That’s why hardware is the perfect place to store low-level security, management, and networking features.
All Intel processors are built with management in mind, allowing administrators to reach below the operating system level for additional security and accessibility. For example, all current Intel Core processors support remote device locking through Intel Anti-Theft (AT) Technology. Unlike pure software Mobile Device Management (MDM) solutions, this approach will work even if a device is corrupted or rooted.

Newer third-generation Intel Core vPro processors (found in newer enterprise and small-business laptops, Ultrabooks and even some tablets) add two-factor PKI-based authentication with Intel Identity Protection Technology, and pre-boot system integrity verification through Intel Trusted Execution Technology (TXT). By using devices themselves as authentication tokens, IT can remove a layer of complexity and cost created by third-party tokens.
Intel builds on this hardware foundation with tightly integrated software. For example, on the security front, McAfee DeepSAFE leverages vPro’s TXT to install security monitoring software below the operating system, while Deep Command provides endpoint management tools for AT and other low-level features.
In some cases, security or management software can run only on complementary processors. In other situations, those processors simply run the software better. For example, Intel has tuned its newer Core processors to support the AES-NI instruction set, which speeds encryption products like McAfee Endpoint Encryption to near real-time. Other compatible systems can certainly run the same program, but processors without AES-NI support could incur up to a 10X slowdown.
The processor is the heart of any device. It may not be the flashiest part of your BYOD strategy, but it’s the foundation. A bit of time considering processor choice during your planning phase can save a lot of money and headaches down the road.
Top two images courtesy of Shutterstock.


















