When you buy an enterprise product, you almost assume nowadays that its management interface is going to be via a Web browser to a built-in Web server on the device. This trend began almost as soon as the graphical Web was available in the mid-1990s, and today almost no one writes their own front-end management software. Well, that is both a blessing and a curse, as the folks from the InfoSec Institute have recently reminded me in their post here this week.

“Under no circumstances should these [Web interfaces] be open to the world and the Internet,” writes the author of the post, using a pseudonym. He goes on to cite a few egregious examples. The issue here is that someone can enter your network without upsetting any of your perimeter defenses, and this someone can use common search tools to find open interfaces using Google and shodanhq.com, a search engine specifically designed to locate web-connected devices. A quick search for open WatchGuard firewalls brings up more than 4,000 of them, for example.
Here is an example of a Cisco router that is open to the Net:
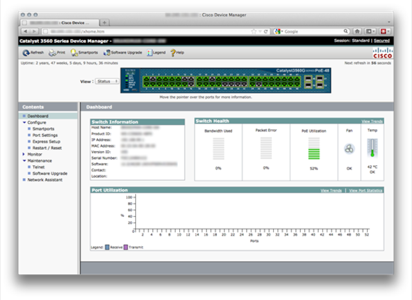
In the referenced blog post, the author shows numerous other examples of ways that hackers can access these open interfaces. Now, you’ll still need to figure out an admin user name and password, but in many instances people just use the default values, making these devices even more insecure.
So what can you do to beef up your Web UI security? Here are several suggestions:
- Disable any optional Web UI if not required. Use SSH if available. Better yet, require that all management happen from a specific PC that is kept in a secure location.
- Restrict access to the Web UI by IP address range or to specific admin IP addresses.
- Restrict access to the Web UI by VPN and keep the device accessible only by private IP on the LAN side of its ports.
- Use a good password. At the very least, use a 26 or longer character passphrase or password for critical network devices. Change it regularly.
- Disable telnet on any Cisco devices, even if the device is only accessed internally.
- Enable brute force prevention or rate limiting. Every layer of security helps.
















