It may not be an independent source of data about Windows, but Microsoft’s system of telemetry for tracking the causes of system failures, is orders of magnitude more sensitive than anything else in the field. A report released by Microsoft this morning reveals that what would have been a record quiet year for Windows security was pretty much wiped out by one stupid little flaw that Microsoft can’t completely patch.

The exploit technique itself is the same one used by the so-called Stuxnet virus, widely believed to have targeted an Iranian nuclear power station. But it is not Stuxnet – more to the point, it’s not the payload used to disrupt Iran, but rather the dissemination method that put it in place to do so. Apparently in the interest of full public disclosure (the fact that not everything should be publicly disclosed justifies the invention of clothes), someone posted the code to the open source repository GitHub.
The exploit in question was responsible for at least three-fifths of some five million malware detections by Microsoft tools in the second quarter of this year. Without revealing any potentially damaging technical information, it uses a malformed Internet shortcut to trick the Windows shell (the system behind Windows Explorer, the file manager – not the browser) to execute the contents of that shortcut as binary code. It’s executed when a USB stick, optical disc, or other portable storage device infected with the virus is inserted into its respective drive. Windows acquires the fake shortcut when polling the device for AutoRun data – for what it can ask the user to run automatically. Since the exploit’s discovery, patches distributed by Microsoft have turned off certain parts of AutoRun functionality, though not everyone bothers to patch.
As Microsoft’s security engineers report, a rise in the success rate of Stuxnet’s predecessors evidently inspired the creation of new variants. Quoting from the company’s 2011 Security Intelligence Report:
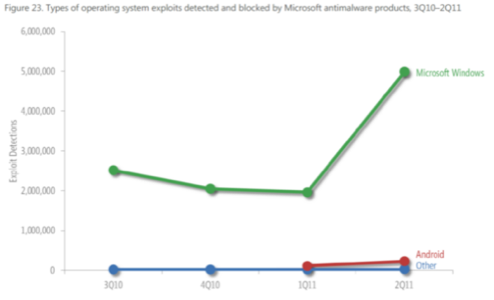
Exploits that target CVE-2010-2568, a vulnerability in Windows Shell, increased significantly in 2Q11, and were responsible for the entire 2Q11 increase in Windows exploits shown [in the chart above]… An attacker exploits CVE-2010-2568 by creating a malformed shortcut file that forces a vulnerable computer to load a malicious file when the shortcut icon is displayed in Windows Explorer. The vulnerability was first discovered being used by the malware family Win32/Stuxnet in mid-2010, and it has since been exploited by a number of pre-existing families, many of which had been designed to spread using malicious shortcut files or by abusing the AutoRun feature in Windows. The CVE-2010-2568 attack mechanism is similar to the techniques already in use by these families, which may explain why their authors chose to incorporate the exploit into new variants.
(The red line in the chart above does not represent relative levels of Android exploits to Windows, but rather the number of exploits intended for Android that Windows was capable of detecting when installation packages were downloaded to Windows PCs from Android Market.)
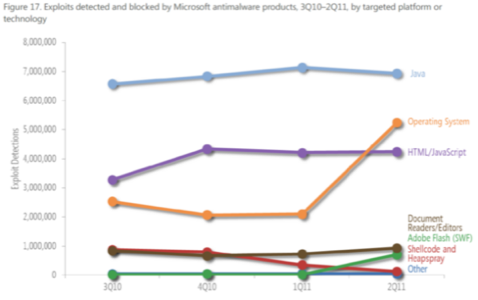
Had it not been for the latest mutation of the malformed-shortcut exploit, Microsoft would have been able to devote a lot of its report to digs at competitors’ platforms. Exploits of vulnerabilities in Oracle’s Java platform constituted as many as half of the exploit detections in Q1 2011 – numbering more than 7 million – though that fraction dropped considerably in Q2 thanks to the shortcut exploit. And detected exploits of Adobe Flash skyrocketed by 40 times, from fewer than 10,000 incidents in Q1 to more than 300,000 in Q2, as a result of maliciously crafted .ZIP files sent in the wake of the Fukushima Daiichi nuclear plant disaster in Japan last April, with Korea-based PCs bearing the brunt of the attacks.

















