It’s a demonstrated fact that as cloud application users find themselves logging on more and more often, they tend to oversimplify their passwords in an effort to avoid writing them all down someplace. It doesn’t help that many IT shops’ first course of action is to standardize identity around social networks such as Facebook, making these public repositories into the lynchpins of private networks’ security strategies.

This morning’s rollout by Ping Identity of a new point release for its PingFederate identity management system is an effort to reorient businesses that have already begun using public identity providers, around a centralized identity scheme that resides back inside the firewall. There, administrators can create policies that govern how users access privileged network resources, based on such factors as where they are, and whether they can also log onto – and authenticate themselves from – someplace else that’s actually stronger.
This latter concept is called authentication chaining, and it’s one of three elements that Ping is touting in its new marketing push around “Adaptive Federation.” Certainly being able to leverage authentication resources from Facebook or LinkedIn expedites the registration process for e-commerce sites. But the strength of that authentication is not enough during checkout, when a logged-in customer may have access to stored credit card data.
So what Ping suggests is a form of chaining that also incorporates a stronger, multi-factor authentication system such as PhoneFactor. An admin may then establish authentication rules that evaluate specified criteria (“Is this a remote user?”) and, if the case is true, chain the process over to that stronger provider. If that provider is unavailable, or if something goes wrong, a separate rule may establish a failover identity provider – someone to trust in the absence of clarity.
“If you have users in multiple directories, and you want to be able to authenticate those users across those directories,” explains Ping Identity technical marketing manager David Gorton in an instructional video published today (above), “you can actually chain those directories together.” This way, after the user provides credentials, the newly enhanced PingFederate system will check them against each directory, until one is capable of validating those credentials. “If he doesn’t get authenticated in any of those directories, he gets rejected,” Gorton continues.
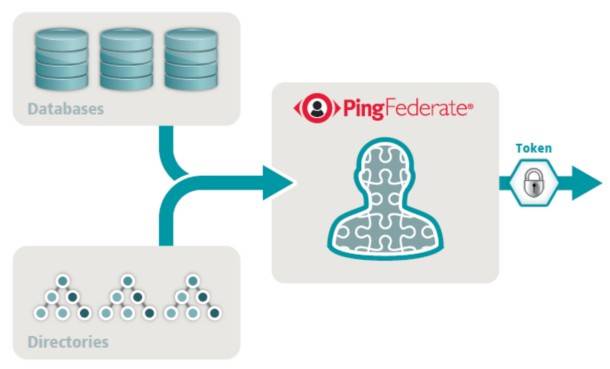
With the third added component, attribute aggregation, elements of a SAML assertion may be combined from multiple sources. This way, for example, when an enterprise stores its employee data in a database rather than Active Directory, PingFederate can collect elements from both sources and piece them together.
“This functionality makes virtual directory products unnecessary for attribute aggregation,” reads a Ping Identity product guide released today. That may not be the best news for so-called identity service providers like Radiant Logic, whose RadiantOne Virtual Directory Server, released last July, manages multiple logons through a centralized console. Radiant and Ping had been partners since 2007 on virtual directory support.
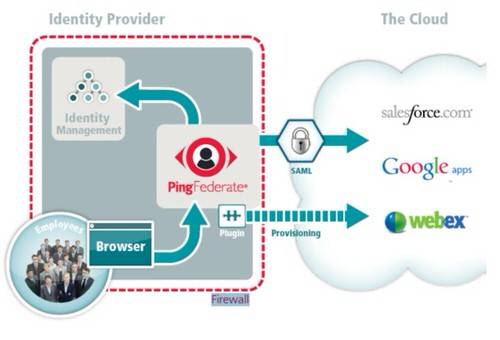
Indeed, back in 2005, Ping CEO Andre Durand went so far as to call virtual directories and identity federation tools “natural product partners.” But that was before providers started moving those virtual directories to the cloud, as services outside corporate firewalls. As the chart above from 2012 suggests, PingFederate remains firmly planted as a public-facing service inside the corporate firewall. While this move isn’t enough to split the partnership, it does place the two companies on different rotational axes, if you will, with respect to where the federation takes place.
Ping Identity is holding a webinar on the new topic of authentication rules and chaining, this Thursday, February 16, at 11:00 am ET. Register here to take part.

















