The Google security team has enabled forward secrecy in its HTTPS services by default, so that captured messages can’t be decrypted retroactively. Even though Gmail went to a secure HTTPS connection by default last year, encrypted files could still be captured in their unreadable form and broken years later, when computers are much faster.

Other HTTPS Google services include Docs and Google+, as well as SSL Web search. All these services are now forward secret when HTTPS is turned on. Initially, only Chrome and Firefox will use forward secrecy by default with Google services, because Internet Explorer doesn’t support Google’s combination of the RC4 authentication and ECDHE key exchange mechanisms. “We hope to support IE in the future,” the security team says.
The forward secrecy enabled today requires that the private keys that maintain the connection to the service are not held in persistent storage. That means a would-be attacker can’t reverse-decrypt past connections. Not even the server operator can decrypt these sessions retroactively. The team has released its work on the open-source OpenSSL library that enabled this security.
You can see whether your connection is secure by clicking the green padlock in your browser’s address bar when on an HTTPS site.
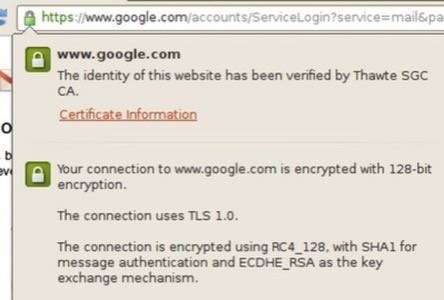
Google’s Progress on Security
Google made encrypted Web search available in 2010, but it did not anticipate that the secure domain would conflict with the Children’s Internet Protection Act, which requires schools to monitor and block certain websites. Since secure search prevented schools from logging, filtering or blocking search results, schools were caught in the lurch. Google resolved the problem by giving secure search its own encrypted.google.com domain.





















