Google has been working to harden Google Apps for its arrival into the enterprise. The tools bring browser based productivity into another dimension.
And, where people are productive, security is to be questioned. In this short review, we look at the new feature Google offers admins and look a bit closer at security in a browser-based world.
To further enable Google Apps administrators, the company has released a new cookie based reset tool for managing security between the client and the enterprise cloud. This functionality of Google Apps allows an administrator to flag a user for re-authentication on their next HTTP request to Google’s cloud apps.
This new feature is targeted at environments where a user of the the Google Apps cloud loses an IT asset and the company wants to remove access to any current for future page requests.
This feature shows how mobile and personal computer are again creeping together in security needs for cloud data service use.
This feature reminds us of the “remote wipe” in MobileMe that is offered for the iPhone. The iPhone version targets removing data from the physical device but for practical purposes is nearly akin to “cookie invalidated” by Google Apps, which forces log-out any active sessions of a cloud based application.
Both features target keeping sensitive information safe and can be activated at any time, killing an active user of the device. Google shares the goal of the tool here:
“Combined with the existing ability for administrators to reset user passwords, this new feature to reset users’ sign-in cookies improves security in the cloud in case of device theft or loss.”
Google goes into a bit more detail in the help file for the cookie reset feature, which describes how to find the feature to reset the cookie (in Users and groups: Passwords) and as an admin remove authorization from any current or future authenticated user or browser client:
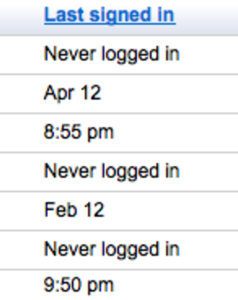
“To prevent unauthorized access to an account, you can reset the sign-in cookies for that user, which has the effect of logging out that user from all current HTTP sessions, and requiring new authentication the next time that user tries to initiate an HTTP session to log in to Google Apps.”
The help file also describes how to find the feature, which shows up in the Users and but in our version of Google Apps (non premium) it didn’t show up in the password section as described.
So far, it looks like this security feature is getting a good response from the administrators that have responded to Google’s blog. We see it as a welcome effort on Google’s part towards preparing their cloud for the enterprise, but also it raises questions of the use of cookies and tying down access to machines (IP) vs. browser cookie.
Securing the browser for the cloud causes us to think of this question:
Are mobile phones (iPhone for example) inherently more secure than computer based browsers?