Facebook enabled a privacy feature Thursday called Trusted Contacts that allows you to select three to five confidants from your friend list to receive the virtual key to your account. If your Facebook is compromised by hackers or you forget your password, these people can supply the codes to get you back in.
The feature was first announced as ‘Trusted Friends’ in October of 2011. “However, we were only testing for the first part of last year [2012], and the feature actually wasn’t available for much of 2012,” Frederic Wolens of Facebook Policy Communications told ReadWrite in an email. “The bulk of our work was making this more proactive (allowing you to select your friends ahead of time) than reactive (selecting your friends after you couldn’t get into your account),” he added.
The Joy Of Facebook Hacking
While there may be some benefits to this feature, Facebook already has two-step authentication, making Trusted Contacts unnecessary in the likely event you can access your email and just use the normal password recovery option. More to the point, Trusted Contacts also pose a big risk. How much can you really trust those Trusted Contacts not to abuse their power?
Remember, it takes only three of the Trusted Contacts’ codes to get into your account. That’s good, right?
Right.
Unless the friends you choose have an affinity for the art of the Facebook hack. In my college years, when shared computers were often accessible in dorm rooms and campus hangout spots, Facebook hacking wasn’t just a prank, it was an art. The rules were simple: If anyone left their account open on any computer that wasn’t their own that person’s Facebook account was fair game. (Sometimes, even that simple rule was bent by the less honorable.)
What typically ensued was a chaotic, hilarious and often line-crossing exercise in testing the limits of friendship. The hack quickly transcended crude status updates and moved into true social media sabotage. Facebook hackers would change birthdays, send unwanted friend requests and write embarrassing notes on walls.
For me, the whole ordeal culminated in a prank where I created a fake profile of my victim, replicated his post history for a week in secret, and then began friending everyone we knew. I mimicked his behavior so well no one figured out it was me for a good day or two. It remains one of my proudest Facebook hacks – and the epitome of my juvenile social media behavior.
Breaking In
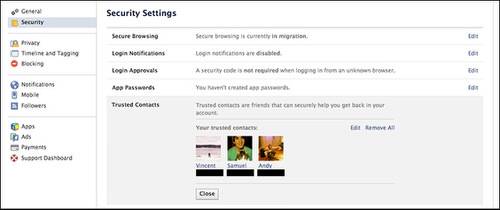
First off, let’s run through how a trio of your Trusted Contacts could access your account without you knowing about it.
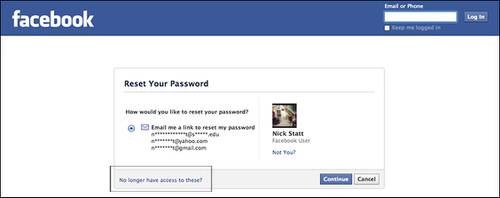
After opening Facebook in a different browser or private browsing mode, a Trusted Friend would click “Forgot your password?” From there, they would identify the victim by name in the Find Your Account field, saying that they no longer have access to the email accounts listed. That lets you put in any email address – and the process moves on without requiring further authentication.
By entering in only one of the Trusted Contacts’ names — in the event that you’re the one doing the hacking, it can be your own name — you can access the code portion of the page. With three codes collected by visiting Facebook.com/recover and claiming the person has reached you by phone, you’re immediately brought to a new password screen where the Trusted Friend can reset the password and gain access to the account.
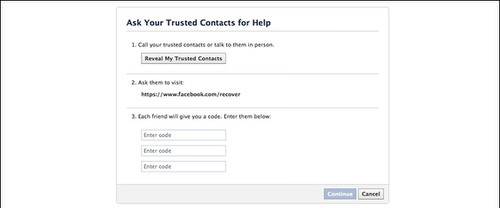
Sounds like it would be a lot of work, and it certainly is when I tried it myself on my own account, but you are essentially handing over the ability for three people, or just one who convinces two others to give them the codes, to change your password without any new authentication required on your end. Granted, you can revoke access to a Trusted Contact, but only from your account.
Who Can You Trust?
Obviously, the best precaution is to pick people you’re confident won’t prank you. But there are also a certain types of Facebook user who should never get this kind of access.
For one, don’t trust anyone who infrequently uses Facebook or who likes to condemn the social network and those who indulge too much in it. The first sign of a weakness for Facebook hacking is disregard for the damage a “Liking” spree can do, or downplaying the importance of Facebook birthdays. These people find it hilarious when dozens of people begin mistakenly wishing you a Happy Birthday.
Conversely, people who use Facebook too much may be just itching to pull off the perfect Facebook prank – and they’ll know the the best, most believable ways to impersonate you.
One smart approach might be to pick two people that dislike each other, making it unlikely that they’ll work together to mess with you.
The simplest solution: Don’t use Trusted Contacts. The feature adds a layer of defense against strangers attacking your account, which could be reasonable considering this year’s surge incidents of malicious hacking. But it also seems like a sly attempt to push the boundaries of Facebook’s importance in our lives.
But by “trusting” your friends enough to give them a key to your digital life, you may be taking an even bigger risk of being pranked, if not actually hacked.
















