Twitter is falling prey to a major security flaw right now. The service is getting swamped with messages that say: “Don’t Click” and a URL. Apparently, this hack has been around for over two weeks, but it only really took off today. If you actually click on the link while you are logged into Twitter, another “Don’t Click” message will be posted to your Twitter account, which then propagates the cycle.

Of course, this is also very smart social engineering. Who, after all, can resist clicking on a link that says “Don’t Click.”
No matter how annoying, though, it doesn’t look like this hack does anything more nefarious than post this message to your account. We will keep this post updated as we get more information.
Update I: Evan Williams just announced that Twitter is working on a fix right now and the messages have now finally stopped.
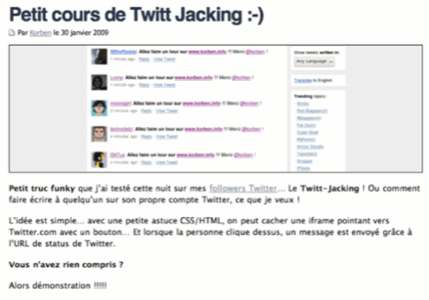
Update II: As one our commenters points out below, this might also be a far simpler hack, where the hacker simply overlays on iFrame over the Twitter status update. While you think you are clicking on a link on another site, you are, in reality, clicking on the ‘Update’ button on Twitter. Looking at the screen shot above, that does indeed seem to be the case. Here is a good description of how this works in detail.
Note: This was our first theory of how this hack worked – turns out, it was way simpler than this: According to Jeff Attwood, this hack could also be making use of a known security flaw called a cross-site request forgery. We are no security experts, but our understanding is that this hack spoofs a request from your browser to Twitter. This only works, as far as we can see, when a service like Twitter allows a user to perform a sensitive action without checking if the user has actually invoked this action (like posting to Twitter) him/herself. If you visit a malicious web site that is vulnerable to this hack, then the attacker can force your browser to send out a request to perform an action on your behalf without you ever knowing about it.
















