PC’s aren’t the only ones vulnerable to Crypto mining hijackers as some malicious sites and infected apps are redirecting millions of Android users to a website that hijacks their phone processors for mining a cryptocurrency called Monero. This process is called Cryptojacking. The site redirects people towards a specifically designed page “performing in-browser crypto mining” after claiming that suspicious web activity was noticed. You are required to enter a code to stop the mining activity, however, after entering the code you will be directed to Google’s homepage. Malwarebytes discovered five internet domains using the same CAPTCHA code and the Coin hive site keys used for the campaign.
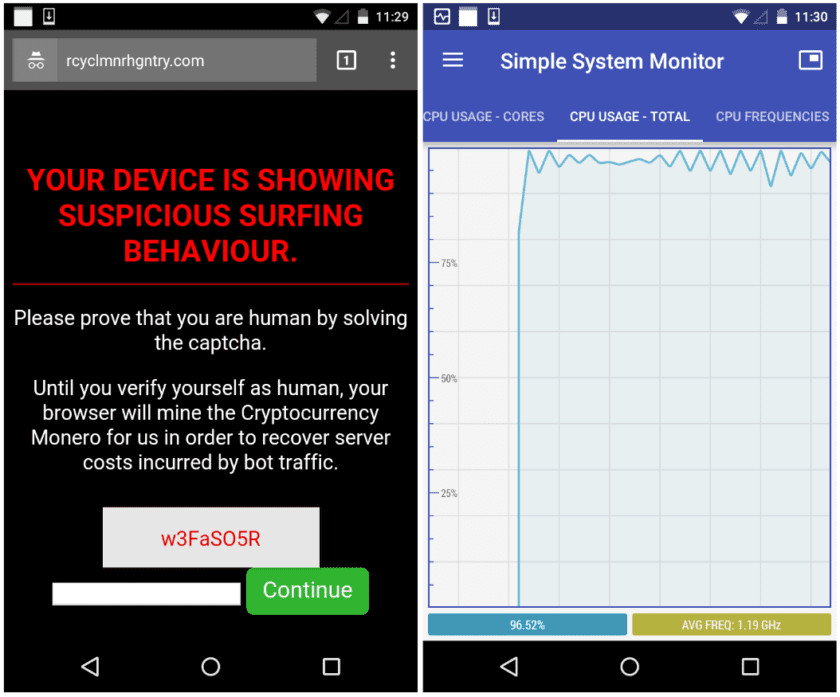
The exact technique used by these hackers is not yet known, but Malwarebytes reveals that the Android devices were hacked so that their phone processors could be used to mine cryptocurrency. Users may likely download infected apps that quickly redirect them to a website and they are asked to enter a valid CAPTCHA code which results in a spike in processor use. Users seem to spend an average of 4 minutes on the pages but that is just about enough mining time. The hackers seemed to have mined a large amount of cryptocurrency as two of the discovered sites had over 30 million visits per month, and the combined domains had more than 800,000 visits per day.
Smartphone users are advised to download apps from Google Play Store alone rather than free downloads from untrusted third-party marketplaces. There is a less likely chance to get infected programs from the Play Store. Google Play Protect has been credited for its ability to spot malicious apps stealing information or allowing hijacks. Last year, Google took down 700,000 apps that were found to be violating its policies. Malwarebytes also recommends keeping your phone safe by using web filters and security software. These Trojanised apps are not the only means through which your smartphones and tablets can be hijacked for crypto mining, your smartphones can also be infected via redirects and pop-unders.