
“Change your passwords now. Like, every password you use on every website you have ever visited.” You may have heard this advice from tech publications and mainstream rags after password leaks were discovered at LinkedIn, eHarmony and Last.fm. It is a good idea to change passwords at least a couple times a year anyway. But the problem does not lie solely with the users. It also lies with the way companies approach password security.
Since the leaks were revealed, tech pundits have been feigning outrage over LinkedIn’s subpar salting and hashing of passwords. In fact, LinkedIn did not salt passwords at all. For the sake of clarity, let’s define what those terms actually mean.
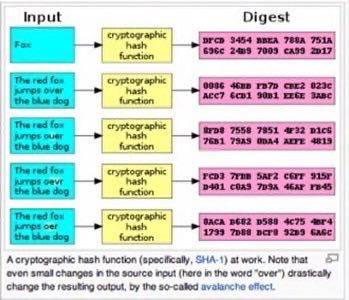
For security gurus, this is kind of like “How to Protect Users 101.” Both hash and salt are cryptographic (code making or breaking) terms for functions that obfuscate passwords in a database, so they can’t be tracked back to a particular user.
A hash is simply a way of organizing large data sets. In the case of LinkedIn and other companies that have been breached, each item within those data sets is a password for a single user. In a cryptographic hash function, which is specifically what we are talking about, the hash is a digital fingerprint for a particular user.
In simple terms, think of it like this:
User + Password –> cryptographic hash function –> unique, unrecognizable data point within a table of data points
It is not enough simply to hash passwords because, at its base, hashing is just a way to organize and randomize data. This is where salting comes in. You have probably heard of terms like 48-bit and 128-bit encryption. These are derivatives of salting a hash. Where the hash creates an identifier (the fingerprint), the salt scrubs the identifier and scrambles it so as to be completely unrecognizable except to an administrator who holds the keys to unlocking the encryption. If a hashed password is salted, then it becomes basically useless to hackers because it becomes much harder to crack and trace to its source. Hackers who look for profit, by nature, tend not to spend a lot of time on projects that are not worth the time required.
Passwords that are hashed but not salted become susceptible to brute-force hacking techniques. The malicious hacker jargon for this (among other things) is SQL injection, a way to hook into a data set and extract information from it.
One of the reasons why so many sites have been hacked and passwords leaked over the past couple of years is because so many security vendors offer the same type of solution. One of the first password “scramblers” out there was called MD5, built by developer Poul-Henning Kamp in 1995. He announced on his blog today that he is letting his product go to end-of-life, and that it is no longer a safe way to encrypt passwords, especially for large sites.
Kamp suggests that large sites not rely on vendors or use techniques with which hackers are familiar.
“All major internet sites, anybody with more than [50,000] passwords, should design or configure a unique algorithm (consisting of course of standard one-way hash functions like SHA2 etc) for their site, in order to make development of highly optimized password brute-force technologies a ‘per-site’ exercise for attackers,” Kamp wrote.
That really gets to the crux of the issue. Companies like LinkedIn, eHarmony, Last.fm and others need to be more proactive in how they manage and secure user passwords. It is not enough to use whatever is available on the market and tack it onto your system. As we have seen time and time again, Internet security is something that companies and users need to be proactive about. For companies, do not take the easy route and trust to fate that hackers will not target your databases. For users, change your passwords, create unique passwords for every site that you use and change them often.
It is easy to blame companies for not securing user information. Rightfully so, if the company was negligent in how it took care of the information. But security is a collaborative effort. As a user, assume that your information is always vulnerable and do everything in your power to protect it.
Top image courtesy of Shutterstock.

















