In the middle of last year, the hacking group Anonymous tried but failed to attack various Vatican Internet servers. A report that was just released by Imperva shows the extent of their prowess, and is a blueprint for other corporate security managers who want to try to protect their own networks in the future from miscreants. While the report itself doesn’t divulge the destination of the attack, it has been widely reported by the New York Times and other news outlets that it was the Vatican.

Of course, it helps that the Vatican used the Imperva Web applications firewall to protect itself and that the logs could be analyzed to see the sequence of events. They state, and we also believe, that this is the first end-to-end attack analysis of this magnitude.
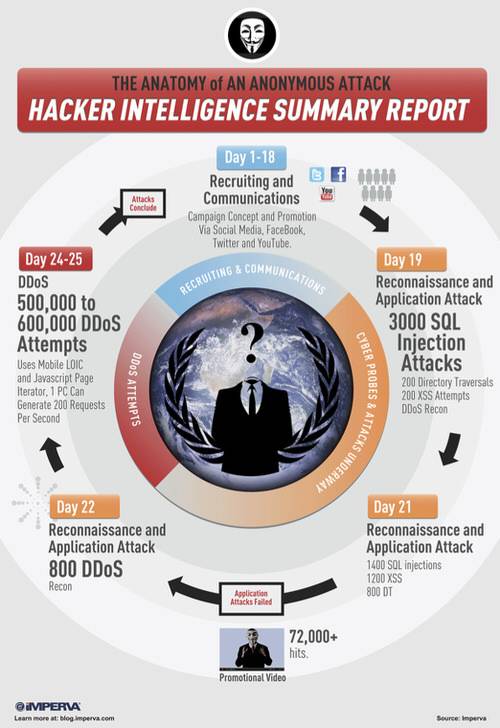
Imperva found that the attack happened over a period of a month in three different phases: recruitment, reconnaissance for an application attack, and a distributed denial of service (DDOS) attack. Various individuals and computers were involved in each phase, including a core group of skilled hackers that Imperva estimates to be no more than 15 people, and a large collection of volunteers to conduct the DDOS attacks from their own computers and smartphones. Anonymous cleverly uses an array of social media accounts for the recruitment phase to find these volunteers. However, this recruitment means that Anonymous is limited in how quickly it can deploy its resources. But it also means that an observant security officer can see whom they are targeting next by watching the forums and social media discussions.
Here is a summary infographic of these phases.
Some of what was observed include the following:
- Anonymous uses the same hacking tools that others use, such as SQL injection and vulnerability assessors, to exploit common website and Web server vulnerabilities. There is no secret sauce. They use off the shelf and cheap tools that are easy to use and don’t require any financial investment. No surprise there. As the graphic here indicates, they used four common attacks.

- They have developed custom attack software. “This allows users to attack sites with mobile browsers. However, their mobile tool, though innovative, is not complicated. In fact, it is probably just a few hundred lines of Javascript code. All it takes for an attacker to participate in the attack is to browse to the specific Web page and leave the page open.”
- “Anonymous will try to steal data first and, if that fails, attempt a DDoS attack,” says the report.
- Even while being under a DDOS attack, “there’s an opportunity for security team to assess the attack details and, if needed, fine tune the rules in order to detect and block the entire attack more precisely.” This is perhaps the best news to date. Coordinating the various volunteers from around the world takes some effort, and a security manager still has an opportunity to step in even while the attack is underway.
- Analyze your alert logs carefully.“The DDoS attack was preceded by a few-days-long phase of reconnaissance. Daily analysis of alert information may help better prepare for tomorrow’s attack”.
- Use IP reputation scoring as part of your toolset. In these high-volume attacks, having the reputation of the originating IP address is helpful to screen and block any harmful traffic and understand the intended purpose of the attackers.

















