While the Homeland Security Department no longer color-codes its threat levels, several security vendors offer up their own dashboards with all sorts of eye candy designed to keep track of which viruses and malware are heading yourway. Here is a brief rundown of the more popular services. All of them rely on agents and collection points scattered across the major Internet peering points and other critical junctions to watch for particular traffic patterns. The idea here is to gain insight into what is happening before something enters your network and starts to hose your equipment or steal your data.

Trend Micro today introduced its Threat Intelligence Manager which uses its database of trends as the basis of several protective, including OfficeScan and Deep Security. The new service leverages the Trend dashboard that can be seen here.
Trend is not the only vendor with such a service. Here are some others that I have used in the past (you are welcome to add your own favorites in the comments, too):
Some of these threat dashboard sites offer more than color-coded icons and long lists of threat descriptions. For example, McAfee’s has an online reputation management system, where you can enter a domain and it will return a host of statistics you can use to judge the domain’s legitimacy.
The TrustedSource site shows you the trends of a particular domain (in this case, Cisco.com) and other relevant information.
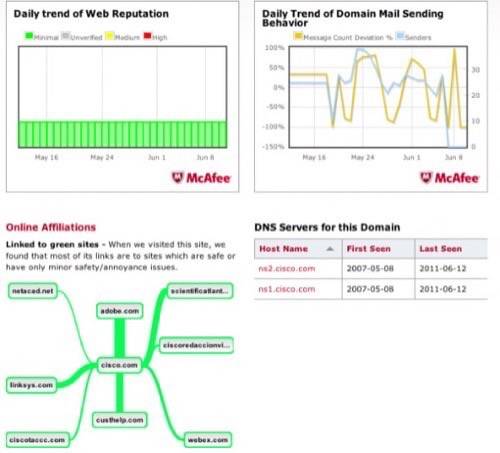
All of these sites suffer from some of the same drawbacks. First, there is the needle in the haystack situation. There are hundreds of new attacks each day and most exploits aren’t really going to do much damage. The few big-ticket items are often hidden underneath the copious number of alarms for the minor ones. For those of you that don’t monitor these exploits, it is worthwhile (and somewhat depressing) to take a gander at one of these sites and see how much garbage is streaming through the average router.
Second, there is no standardized virus or threat naming system, so the same threat can be called completely different things by each vendor. This makes cross-site comparisons almost impossible until a virus gains enough notoriety that the press can bring some kind of consistency. Of course, by the time the press gets a hold of something, it might be too late for you to do much about it in terms of protecting your network.
Finally, if you are trying to find a particular patch or security bulletin, you might be better off Googling it than trying to track it down on each site.





















