Several weeks ago, when the Stuxnet virus first struck, the thing that stuck out was how it targeted the computer systems found in factories, called supervisory control and data acquisition systems, or SCADA. My first thought was a hacker had picked a unique target in order to show off his or her chops.

My second thought was how this type of attack could herald a type of economic warfare we don’t think that much about any more in an era of electronic communications. To preserve our societies, we need to be able to continue to make things. This virus would attack a country at that level. But now, some experts have suggested the virus shows “signs of nation-state involvement” as it apparently goes after the control systems in an Iranian nuclear facility.
In fact, this was not the first SCADA attack. Last year, hackers got into the SCADA that countrols U.S. power systems. It was possible that foreign powers, probably Russian or Chinese-directed hackers, were behind the infiltration. Given the relative weakness of anti-virus technology in SCADA, versus traditional business systems and consumer electronics, it was just a matter of time until someone figured it out.
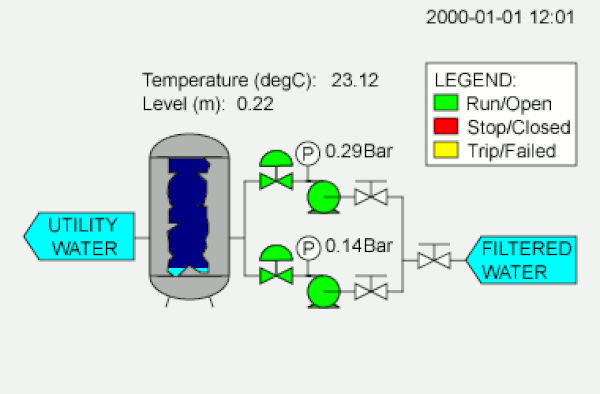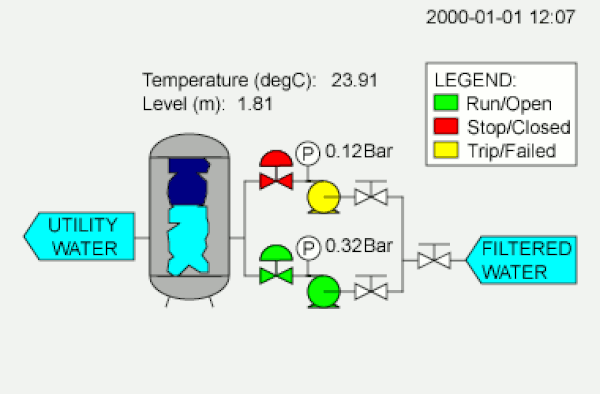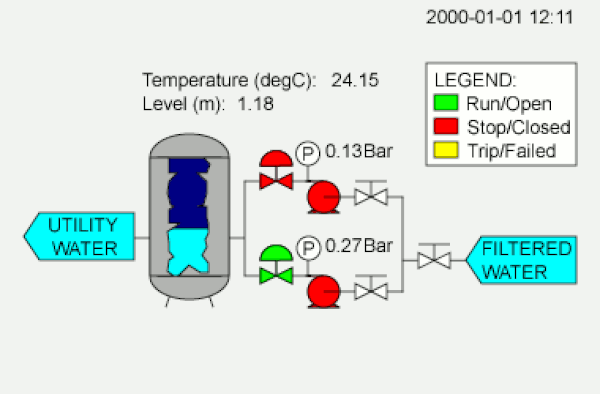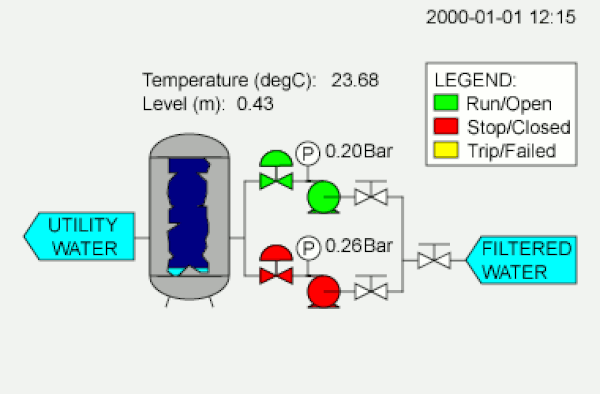
Most attacks on computer systems, Threat Post reminds us, are predicated on sweet, sweet money. The Stuxnet virus has no immediately visible paths to cash dollars. It is also not just a clever virus, but a very sophisticated one. These elements together have convinced security specialists that it has a national backer.
“The attack exploits a zero-day vulnerability in the way that all currently supported versions of Windows handle LNK files and is spread initially through USB sticks. Once an infected USB drive is attached to a PC, the attack on the machine is essentially automatic and there is little indication to the user that anything bad has happened. But that’s just one piece of the puzzle. Stuxnet also exploits a vulnerability in Siemens’ WinCC SCADA control software, which runs on industrial control systems in utilities, power plants, manufacturing facilities and other key environments.Once on the machines, the malware attempts to contact a remote server and join a botnet.”
Another element that hints at national origin is its alleged attack on the Bushehr nuclear plant in Iran only weeks before it is supposed to go online. A journalist friend of mine in the Middle East did remind me, though, that information out of Iran is rarely accurate. If it is true, it could point to the involvement of the Israel, who have been vocal in their opposition to Iran achieving nuclear capability. The regime has threatened to destroy Israel and is within striking distance. Other suspects include the U.S., Saudi Arabia, Pakistan, the U.A.E., well, really, anyone in the area. And many outside of it.
Stuxnet has attacked 45,000 systems so far and probably took a team of about 10 hackers to create.
U.S. military computer systems are probed thousands of times a day, so viral warfare is an established element of international relations. You have to wonder when the first Chernobyl-sized hash will get served.
Atom bomb photo via Richard John Jones | SCADA diagram and Iranian nuclear logo from Wikimedia Commons





















