Security researchers from various companies have uncovered the latest cyber weapon, nicknamed Sykipot. It appears to try to grab documents from high level executives within a variety of target organizations, of which the vast majority have been defense related agencies working on unmanned combat drones. The origins of the attacks appear to be with a long-standing well-funded Chinese group that has been operating for several years.

The best explanation of what Sykipot is doing is from AlienVault here, although there is additional information from Symantec and Trend Micro as well. All agree that while the attacks aren’t super-sophisticated, they represent a real threat.
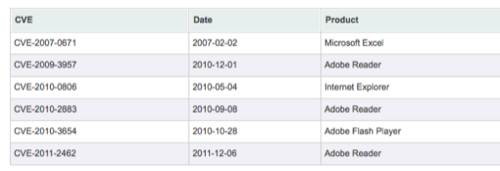
In the recent attack, when the malicious PDF is opened, the Sykipot malware is executed and the user is shown a copy of a clean PDF file before Skyipot is injected into iexplore.exe, outlook.exe and firefox.exe, if they are available on a Windows PC. The Adobe Reader vulnerability (which carries the reference number CVE-2011-2462) is just the latest in a long string of other exploits by the same authors that go back to 2007, including embedding malicious Javascript into PDFs and another Adobe zero-day vulnerability that was recently patched. (See below.) That is very scary indeed. Many of the researchers predict that this isn’t the last time we’ll see Sykipot come through looking for more information.
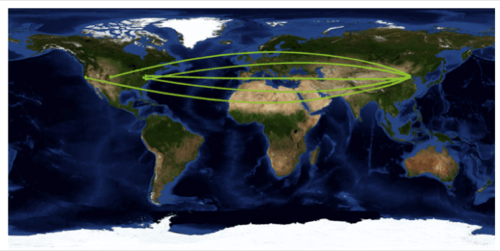
The AlienVault security blog post shows how this malware operates, and how they have tracked it back to a Chinese Web server vendor Netbox, and a series of Chinese ISPs and proxy servers, along with its command-and-control sites that are also in Chinese IP address spaces. Netbox allows developers to compile and deploy ASP apps into standalone .EXE files. Here is its map showing the redirection to Chinese source addresses:
AlienVault researchers state: “We shouldn’t jump to assumptions, but whoever is behind Sykipot is massively collecting information from targeted victims that cover dozens of industries. [While] it’s true that the piece of malware isn’t too sophisticated; it is related to at least six zero-day attacks that require skills and/or money. Anyway we have been seeing that ‘not too sophisticated malware’ works.” They conclude their blog post with this ominous bit: “Someone has said that cyberwar does not exist. Draw your own conclusions.”





















