

Securing a Bring Your Own Device (BYOD) program means more than hoping endpoint authentication will keep out the bad guys.
BYOD security is a big deal. In 2012, Intel surveyed 3,000 IT decision makers and 1,300 end users from Australia, Germany, South Korea and the United States to better understand their BYOD challenges. In three of the four countries, IT Managers considered a lack of security features the most important factor inhibiting device adoption. German IT managers ranked it second, after only government compliance.
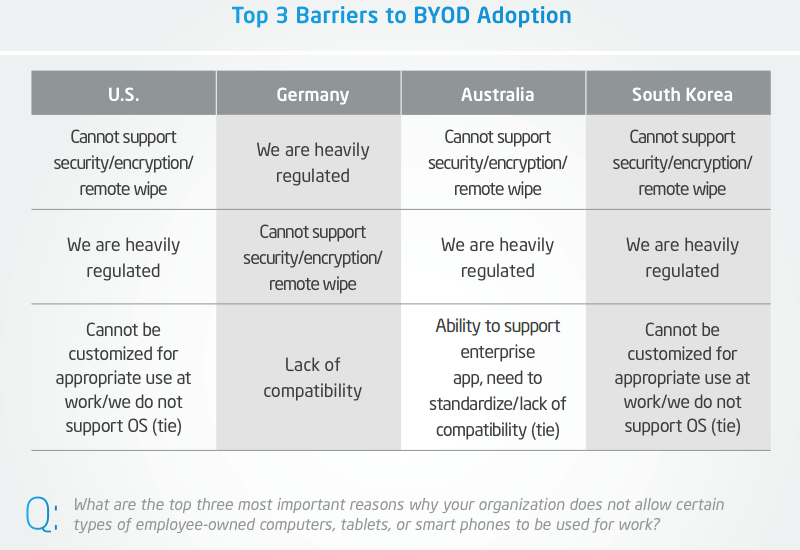
BYOD may be inevitable, but the security concerns around it are well-founded. Some of IT’s top BYOD security issues are beyond the ability of software-management tools to handle alone. These include
- Unlicensed Software: Owner-installed applications on personal devices can violate enterprise license agreements, and others could compromise the integrity of your network.
- Unsecured Third-Party Connections: All smartphones and most tablets can connect to unsecured wireless networks, offering an unmonitored back channel.
- Malware: Devices can become infected outside the firewall through non-work usage.
- Rooted Devices: By gaining root access to mobile devices, users can bypass security restrictions and, in some cases, install rogue apps.
- Lost, Stolen, Or Damaged Devices: When devices disappear or go out of service unexpectedly, businesses can lose access to critical data. Furthermore, in addition to compromising local data, stolen devices can expose the entire network.
Each device class and user type brings unique security challenges. To address them all, IT needs to leverage software and hardware solutions to lock down and manage devices while simultaneously securing the data itself. Here are three steps to help make the BYOD environment as secure as it can be.

1: Educate Employees
Curbing dangerous behavior is the first step toward reducing risk. Personal device management policies and procedures help reduce your company’s risk with very low cost and complexity. In a review of its own, internal BYOD program, Intel noted three types of employee education necessary to minimize risk:
- User Training: Training end users about the content and ramifications of the employee service agreement and sharing best practices for data protection inside and outside of the office.
- Security-Desk Training: Training the Help Desk to answer questions quickly, efficiently, and within the allowable legal scope created by the program.
- Developer Training: Training developers to build secure data access and storage into their application code.
With its favorable cost-benefit ratio, education is low-hanging fruit. In the IT manager survey referenced earlier, managers from all four participating countries that had begun securing their BYOD systems had most commonly implemented device management rules and an employee code of conduct. Employee education is a rewarding place to start, but – based on the fact that security concerns persist – it is obviously not a standalone solution.
2. Secure Your Data
Tomorrow’s devices could be completely different, future applications may handle data in entirely new ways and users will always find ways to use devices inappropriately. Future-proofing your network against the unknown requires a shift from protecting devices to protecting the data they use. Encrypting and backing up data is essential, but IT should also consider other, complementary methods of making sensitive information less accessible.
One popular software-based security method gaining steam in BYOD environments is the Virtual Hosted Desktop (VHD). VHD (sometimes known as Virtual Desktop Infrastructure, or VDI) creates a complete desktop image that includes an operating system, all applications and settings. The hosted desktop can be accessed from any compatible machine, and processing and storage take place on a central server. With enough network bandwidth and powerful hardware, this type of virtualized environment can combine acceptable performance with high-levels of security.
For high-security environments in which manageability and recovery trump everything else, it is often the default computing paradigm. But for most BYOD workers, VHD’s drawbacks usually outweigh its advantages. VHD cannot take full advantage of all the features of local hardware, and it performs poorly on marginal networks – a major issue for remote workers. Furthermore, the desktop paradigm may break down on non-PC devices, limiting the available audience.
Containerization is way to address VHD’s issues by placing native applications inside a safe zone on a device. A virtual machine manager (VMM) abstracts the container from the client hardware, boosting performance and reducing server strain by allowing client-side execution – while still improving security by isolating the container from certain functions, such as wireless network connections, USB ports or device cameras. Some virtual containers contain an entire operating system and productivity application suite, while others are purpose-built, single-function virtual devices that provide services like compliance monitoring or highly secure applications.
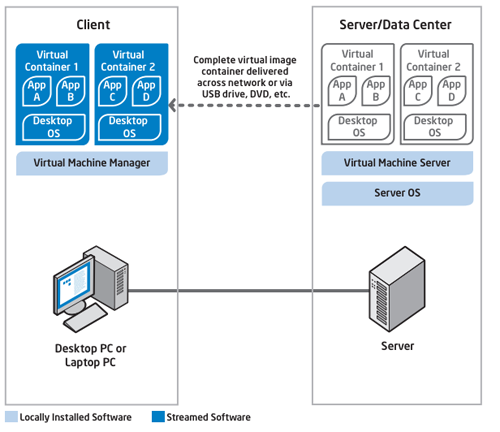
IT can create or purchase containerized applications for every platform, including smartphones, providing a much broader client base than VHD. Containerized applications also run at or close to the speed of fully native applications, and caching lets users continue working through network disruptions. However, containerization can compound development and administrative burdens, and since containerized apps require client-side storage, they are inherently less secure than fully virtualized solutions.
3. Use Your Hardware
Selecting the right subset of hardware to support will bolster software-based security measures while lowering management costs. For example, if a company chooses to support a variety of Intel-based devices, IT could implement a 100% Windows-based environment. This would reduce the cost of developing and securing applications for different platforms while allowing IT to leverage Windows’ existing security infrastructure, virtualization tools and anti-malware. And it would still allow employees a wide choice of devices to meet their individual needs.
On an application level, properly chosen hardware can augment your management tools. Mobile Device Management (MDM) software can identify devices that are out of compliance, but it has limited reach into rooted, broken, hacked or otherwise compromised systems.
Chipset-level security technologies like Intel VPro (found in 3rd-generation Intel Core processors) allow MDM to reach underneath a managed device’s operating system, performing remote wipes and pre-boot virus scans, regardless of the device’s status. By providing access below the operating system, VPro allows administrators to correct problems by loading software patches and virus definitions, and its integrated support for Public Key Infrastructure (PKI) allows IT to use the devices themselves to authenticate users, removing the need for third-party software tokens or hardware-based authentication devices. Intel Anti-Theft technology extends security features such as remote, OS-independent device locking and unlocking to earlier processors, as well as newer, VPro-compatible chipsets.
Finally, selecting the right hardware can make other software options more viable. For example, VHD’s biggest drawback is performance. Hardware that accelerates common virtualization tasks can mitigate that sluggishness, making the security of VHD more acceptable to users.
Securing BYOD will always be a challenge, but with the right planning and proper device selection, IT can make users’ hardware work for the cause, rather than against it.

Lead image courtesy of Shutterstock.





















