Editor’s note: This is the second story in a three-part series by Alex Korth on privacy. Read the first post: On Privacy in Social Networks: What Drives Users?

Most of the time, providers of social networks are commercial enterprises. Developing, bootstrapping and running a social network comes with very high costs, but most services do not charge their users and instead choose different revenue streams. Unfortunately, the meanings and consequences are not questioned by many users. As Andrew Lewis famously wrote, “If you’re not paying for something, you’re not the customer; you’re the product being sold.”
As mentioned before, most providers of social networks (especially non-business social networks) run their services as ecosystems to generate content and knowledge around their users with the intention of attracting advertisers and application developers. Since only a minority of users contribute the majority of content, providers carefully optimize their sites such that the flow of this valuable user-generated content is maximized. This means that providers intend content to have as many recipients as possible. But this strategy is quite contrary to the goal of most users, who need transparency and control over the reach of their content and information. As a result, there is a need to limit the audience of posts, especially when it comes to private content. These contradictory goals lead to the following problem areas on the provider side. (See “On Privacy in Social Networks: What Drives Users?” to view the problem sources on the user side.)
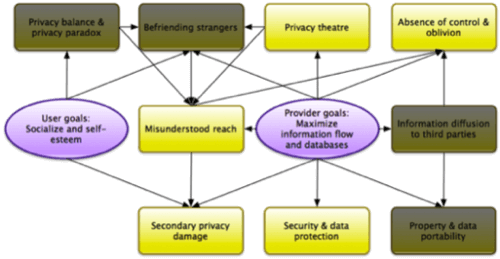
3: Privacy Theatre
Privacy Theatre describes what’s observable when reading provider statements in the press: What’s promised and what’s provided are sometimes not the same. There is a trend to escape criticism from privacy fundamentalists by providing features to control privacy, as research has shown, whilst making these controls hard to use and find. Also, privacy policies are usually not read or understood by ordinary users. No wonder: They are often obfuscated by legal jargon.
4: Misunderstood Reach
Following the before-mentioned contradiction of party goals, it is no wonder that on many networks, it’s not quite clear for users where content flows. Since, in contrast to the offline world, every provider defines its own rules of information flow, the truth is a combination of settings, friends and privacy policy, and consequently is hard to comprehend. With the Privacy Theatre in mind, I assume that providers could easily offer clearer transparency. However, the critical aspect of missing transparency is that without it, all offered control mechanisms are less effective.
5: Absence of Control & Oblivion
The lack of transparency concerning the content reach for the sake of information flow often comes with a vacuum of easy-to-use controls for users to steer the accessibility of their information. This implies a definable lifetime and an easy way to delete information, which is featured rarely. Controls are often dislocated somewhere in deep menus and deletion mechanisms often take several clicks and/or do not really erase things.
“We assumed the digital footprints we left behind – our clickstream exhaust, so to speak – were as ephemeral as a phone call, fleeting, passing, unrecorded… [In fact,] our tracks through the digital sand are eternal.” – Tom Zeller Jr.
6: Secondary Privacy Damage
Without a proper transparency of the consequences of activity, users inadvertently threaten other individuals’ privacies without their knowledge. Common examples include:
- Uploaded address books: Sure, it is a handy way to have a provider find friends, but often, these addresses are not deleted on the other side. Private information and social connections are disclosed, without any permission of the threatened individual.
- Identity linking: By, for example, tagging a user in a photo, sensible information may be revealed.
7: Security & Data Protection
One should not forget that there are additional technical aspects that might get problematic with respect to user privacy. The aspects include:
- Threats and risks through wrongdoers accessing private information.
- Security flaws and implementation errors from the side of the social network.
- Social graph privacy threatened through computational attacks to private information via the friendship connections and group membership of the user.
The last and final part of this post series takes us to a meta-level: What problem areas arise from third parties coming into play?
Now that you’ve seen seven of nine problem areas of my taxonomy: Did I miss something? Please leave your thoughts in the comments!
Login photo courtesy of Shutterstock.










