As a retailer, shoplifting is an ever-present concern. No matter what you try, there will always be a group of people that can find their way around whatever security measures you have put in place. It is a cost of doing business. It is much the same way for mobile developers. While most people will play by the rules, there will always be a group that is stealing your product. They are often armed with jail broken and unlocked devices and can have a profound effect on a developer’s bottom line.

Jail broken devices are the prime source of software theft for mobile app developers. Fiksu estimates that 10% of iPhone and 7% of iPad users have jail broken their devices. Once jail broken, iOS devices are much more capable of stealing software and can cost developers up to 40% or more of their revenue. Thieves will always find a way to get want they want but diligent developers can limit the impact of their bottom lines.
“I think that there are predominately two types of theft that occur. It all starts with the jailbroken device. I think it is really critical to note that not all jailbroken device users are thieves. I think the vast majority of jailbroken device users are substantially similar to typical device users. It the select few that are software thieves,” Palli said.
“Most customers are great customers but you have to be aware of the fact that some thievery can take place and you need to be aware that it can occur,” Fiksu VP Craig Palli told ReadWriteMobile. “If it ends up being 1% of your revenue slippage, you may decide that it is not worth the cost to monitor it. There are cases where it can be 40% of your revenue and all of a sudden that is a real issue that requires some amounts of diligence and time.”
Fiksu, a Boston-based mobile app measuring and marketing company, defines app software theft in two ways when it comes to jailbroken devices. For paid apps it is jailbroken users downloading “cracked” apps on third-party stores like Cydia and AppTrackr. For developers that rely on in-app purchases for freemium titles, software theft occurs when a jail broken user can buy a good in the app but circumvent the payment processors.
“I think what is really interesting for the typical entrepreneur and even the developers within larger organizations developing apps, I don’t think when start at the outset creating a mobile app program that they consider theft to be an issue that they should be thinking about,” Palli said. “It is really off the radar screen and it is one of those things that if you are not paying attention to it, it can bite you.”
There is no silver bullet to stopping software theft from jailbroken devices. Like any business that sells a good, there needs to be a system in place to combat the problem. Palli says it is a three-step process: recognize the theft, measure how much it affects your business and manage the problem. Recognizing and measuring are the easy part. Managing requires diligence and testing.
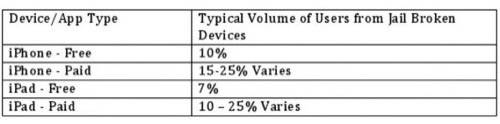
For instance, with a paid app, do jailbroken devices steal your app 1% of the time or 40% of the time? For freemium apps, how often are jailbreakers stealing in-app goods? Palli says it is a matter of determining what is healthy and unhealthy behavior coming from jailbroken users. If you notice that 6% of your users come from jail broken devices, a healthy interaction with the app should be around 6%. If 6% of your users are jailbroken but making up 30% of the interaction, it is likely some of them are stealing. It is possible that those jailbroken users are just friendly power users but there is also a higher probability that they may be thieves as well.
When it comes to cracked apps and third-party app stores, there is very little the individual developer can do. Apple has started sending take-down notices to third-party stores like AppTrackr and it is in the best interest of Apple to protect its developers by making sure their content is not pirated or delivered for free to jailbroken users. For freemium apps it comes down to developer diligence. Palli recommends that developers should set up systems to see if they can steal their own content.
“It is not enough to just plug into one of the many transaction processing organizations out there and just assume it is going to work. You need to plug in and diligently test the theft,” Palli said. “Literally test it yourself. Can you trick the system, can you find a way to get in-app goods for free? If the answer to that is yes, amongst the community of software thieves out there, they are going to find a way to do the same things.”

In terms of user behavior, Palli does not think there is much of a difference between iOS and Android users of jailbroken and unlocked devices. For Fiksu it is easy to track jailbroken iOS devices and behavior because of how everything is funneled through the App Store. Android is a much more divergent model that it is more difficult to track. Is there a higher instance of theft for Android developers? Perhaps. Android developers also have to worry about piracy of their apps that is not really a problem with iOS.
What types of apps are software thieves targeting? Social networking, travel and games are the most common. Technology apps that provide a service like Web browsing or storage are often targeted as well. That would make sense as jail broken users tend to be more technologically savvy and have very specific purposes for jailbreaking their devices.
While jailbroken users are the primary source of theft, Palli cautions lumping them all into one group of bad people. Also, to note, while some may call this theft, others call it copyright infringement. Either way, money that was going into a developer’s wallet did not.
“I think the most important thing to realize in the perception in the market is that all jailbroken device users are in some way nefarious or bad. That is just not the case. Most jail broken device users from the app developers’ perspective are great users and are just like users of non-jail broken device users,” Palli said. “Unfortunately there are those that seek to commit software theft. Those are the ones we need to be worried about because in aggregate, those are the few that can impact any one app developer significantly and I think that is really the crux of the matter.”




















