A phishing attack aimed at new Mac users was launched the week after Christmas looking to obtain the credit card information of people signing up for a new Apple ID. The well-timed attack tries to redirect users signing up for an Apple ID to a phishing site designed to look like the Apple sign-in page asking users to update their account information.

Security firm Intego found the attack and posted the information on its company blog. The phishing email comes from [email protected]. This should give users their first pause as all Apple emails come from the @apple.com domain. The next red flag is that the URL that users are getting redirected to is not an apple.com email address but rather goes to a numbered IP address.
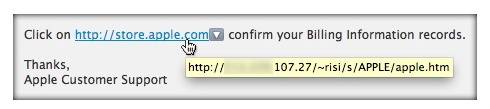
Source: Intego
The sign-in page asks for users profile information, including the credit card information that is tied to an Apple ID account.
One of the first rules users should be aware of when checking for malware and spam in email is to hover over a suspicious URL with to see the location of the URL they are about to click. Tell tale signs of phishing, malware and malicious sites are when the URL does not appear to be headed to an official page from the company in question.
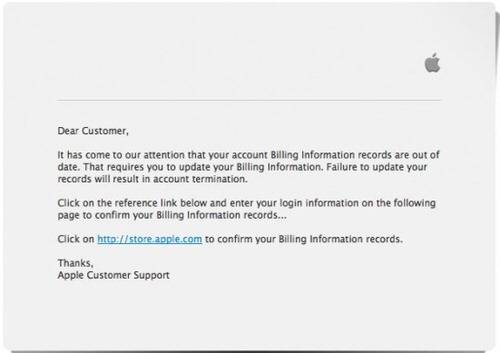
The phishers behind this attack have likely been sitting on it a while, waiting for when users received new Apple products during the holiday season. Malware makers are very sensitive when it comes to the timing of attacks. Zero day hacks are often stockpiled and unleashed when the impact will be optimal. Other malware and spam attacks are saved up for big news stories, such as what was seen during the Japan earthquake in 2011 or the death of Osama bin Laden. Spammers will then hit search engines with poisoned results and attempt to fill email inboxes with links to malicious sites. While the phishing attack aimed at Apple users was not a zero day attack, it is an example of phishers knowing when the best times are to launch an offensive.
Did you encounter an email similar to this last week? What other phishing attempts have been made against your inbox recently? Let us know in the comments.










