Do you have users who have more rights to network resources than they should have? Chances are the answer is yes. A new study from Ponemon and sponsored by HP along with another paper sponsored by Symantec point out the old security saw that the threat from within is still real and still a big deal. Maybe it is time this holiday season to finally clean up your network’s access rights.

These privileged users, as Ponemon calls them, include database administrators, network engineers, IT security practitioners and cloud custodians. (Now there is a job title that brings up all sorts of interesting imagery.) A majority of them “will look at an organization’s most confidential information out of curiosity,” not because they are trying to do anything nefarious with this information.
This isn’t new. But it is instructive nonetheless. Here are some of the problems Ponemon outlined in their findings:
- Not revoking privileged access status after the employee’s role had changed and providing everyone at a certain level in the organization with such access. This includes terminations too, where 17% of the respondents say this situation is likely to happen.
- Not checking a request for higher-level access against security policies before granting the request.
- No single, unified view of access rights and policies across the enterprise. In the study, “39 percent say assignment is determined by well-defined policies that are centrally controlled by corporate IT and another 13 percent say it is determined by well-defined policies that are controlled by business or application owners.”
- Many organizations say that they cannot keep pace with the number of access change requests that come in on a regular basis, despite using a variety of automated authentication and security management systems.
- Mobile apps represent the greatest risk for access right violations, according to 43% of those surveyed.
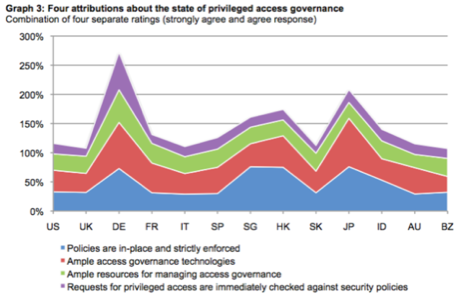
- The potential for privileged access abuse seems greatest in France, Italy and Hong Kong, according to respondents in those countries. Germany and Japan seemed to have the tightest controls. Ponemon surveyed 5,569 IT operations and security managers in 13 countries.
Symantec’s paper, called “Behavioral Risk Indicators of Malicious Insider Theft of Intellectual Property,” covers the shady size of insider threats. It can be downloaded here (registration required). It was written by Dr. Eric Shaw and Dr. Harley Stock, experts in the fields of psychological profiling and employee risk management.
“FBI reports confirm that insiders are a major target of opponent efforts to steal proprietary data and the leading source of these leaks,” according to the study announcement. “The majority of IP theft is committed by current male employees averaging about 37 years of age who serve in positions including engineers or scientists, managers, and programmers.” Moreover, “about 65% of employees who commit insider IP theft had already accepted positions with a competing company or started their own company at the time of the theft.”
“Most insider IP theft was discovered by non-technical staff members,” say the authors. Common techniques to steal information aren’t fancy: we are talking emailing data or using file transfers. They recommend better employee screening, implementing data loss prevention tools, and firming up security policies and making sure they are implemented correctly.
Common sense, but scary stuff, indeed.










