It was a question so seemingly obvious that even Congresspeople found themselves asking it last week: If “the cloud” is one place where multiple files and resources are pooled together, then what’s to keep it from becoming the one target for malicious attacks and corporate espionage?

The emerging layer of cloud operating systems with Linux kernels provides hardware-level support for conventional server OSes such as Windows Server, which are now free (or at least more free than they were) to concentrate on running applications. The problem is, the more advanced systems for maintaining user privileges, auditing activities, and organizing resources are in the virtual OS, and not the one doing the virtualization. So the person in charge of the virtual OS may become the weak link in the chain.
“Managing the administrators of that environment is absolutely critical,” says Nimrod Vax, who directs product management for CA Technologies‘ security business unit. “The administrator of a [VMware] vCenter console pretty much has full access into the entire IT environment, and can manage all of the VMs, change configuration, copy them with the sensitive information that’s on them. That can have a lot of impact, both from a business and a legal perspective. The need to segregate duties of these administrators, manage their privileges, manage shared accounts in those environments, audit what people are doing, all of these capabilities and requirements that are strong in any regulated environment, need to be more so in the virtual environment.”
Suddenly, data centers that were in perfect compliance with government security regulations find themselves in danger of losing that compliance as they move to virtualization, where a new layer of abstraction introduces a separate order of operations at a lower level.
Moving security further downstairs
Last August, CA entered into an alliance with HyTrust, which makes both software and appliances for virtual infrastructure security. This morning, that alliance has borne fruit in the form of CA Access Control for Virtual Environments, an extension of CA’s existing privilege management and auditing platform into the virtual layer, as well as an extension for vCenter.
[Screenshot courtesy CA Technologies]
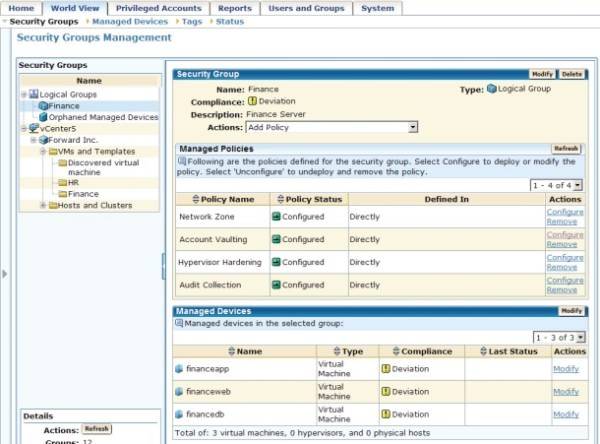
“The virtual environment introduces some elements that are not there in the physical environment,” explains CA’s Vax. “By definition, when those physical environments, with the physical controls that are already in place, in many cases even our own software, move into the virtual environment, you’re introducing another layer of infrastructure. That infrastructure comes with its own group of administrators. You usually have system admins and application admins, and you separate the duties between them; now you’re introducing the virtualization administrator. And that layer also needs to have separation of duties as well.”
By way of vCenter, the new CA Access Control provides similarly auditable, temporary (i.e., time-sensitive) access controls to designated administrators as the product has previously provided for the physical layer. Also, using the emerging CloudAudit standard, the new system provides similar auditing capabilities for devices and resources that provide the infrastructure for the virtual environment, as CA has provided before for physical.
“With virtual infrastructure, and the hypervisor in particular, you now have access to networking, storage, and server resources all through one single platform and application,” says Eric Chiu, founder and president of HyTrust. “If you don’t have proper controls, you actually create a lot of issues, [particularly with] slowing down the ability to automate.”
Dis-inhibiting automation
The whole point of virtualization from Chiu’s perspective is automation, the bit about increasing utilization and adding scalability is all by way of taking the processes of automating functionality and automating them. Without those controls in place, he explains, this automation never happens. “You now have lots of administrators who need to access this environment – networking, storage, ESX, VM, desktop. And without being able to provide them the adequate levels of permissions for what they can do within the environment, but restrict them only to those permissions and specific resources they’re allowed to manage, and have that automatically built into the infrastructure, you end up having to put a lot of rigid controls in place.”
And CA Access Manager isn’t rigid? No, not with comparison to what Chiu sees every day. There’s an emerging practice called air gapping, a phrase borrowed from plumbing, where entire environments are kept intentionally non-networked to one another as a security measure. Perhaps less rigid is a policy of delegating lower-level admin authority over virtual environments to a trusted few, people who can be trusted to work overtime. Some executives hire family members for these critical jobs because, of course, you can always trust your family. Large organizations that should reasonably have 20 to 30 administrators on a nationwide level, end up having as few as two or three.
[Screenshot courtesy CA Technologies]
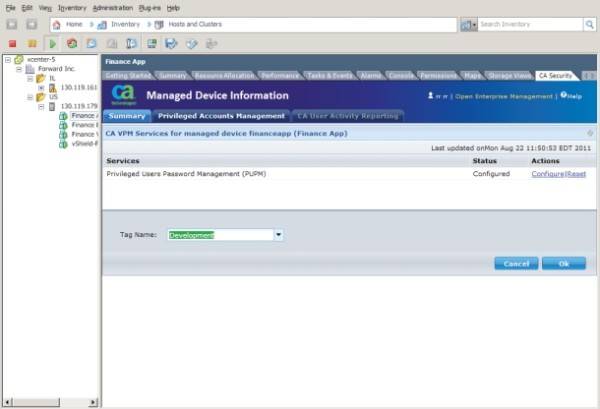
“With proper automated controls in place, you can truly scale your environment,” remarks Chiu. One of CA’s and HyTrust’s pilot customers for the new Access Control is a globally recognized Fortune 25 insurance provider which had precisely this problem, said Chiu: It was incapable of scaling its virtual infrastructure up because it could not hire what it perceived as enough trustworthy virtual-level administrators.
“There are a lot of challenges that customers are going through, in terms of maturing in their use of virtualization, and creating IT-as-a-service,” the HyTrust president continues. “These challenges end up slowing down adoption… This is the first solution I’ve seen that addresses end-to-end needs of securing the virtual infrastructure that all these VMs now run on, as well as securing the virtual machines inside, while having all that be pre-built for dynamic, virtualized environments.”
The current Access Control is built around VMware and vCenter, though CA’s Vax says it’s a “non-issue” to extend it to cover other platforms as well, with the goal of being recognized as truly platform-agnostic. However, while there’s growing activity surrounding OpenStack and OpenNebula, HyTrust believes that broader industry adoption of these open source alternatives to VMware vCloud Director is at least two years away.





















