The FBI is being accused of planting backdoors in the security-focused open source operating system OpenBSD. OpenBSD is used in commercial security products such as firewalls from Calyptix and .vantronix. Thus far, a code audit has not revealed any backdoors in OpenBSD but some bugs have been found.
Earlier this week, OpenBSD founder Theo de Raadt forwarded an e-mail from Gregory Perry, former CTO of the defunct security company NETSEC, to the OpenBSD mailing list. NETSEC paid developers to contribute to OpenBSD during the 90s. Perry claims that former NETSEC developer Jason Wright and his development team inserted backdoors into the OpenBSD Crypto Framework under the direction of the FBI – a claim Wright firmly denies. Perry claims to be coming forward now because his 10 year nondisclosure agreement with the FBI has expired.
From Perry’s e-mail:
If you will recall, a while back I was the CTO at NETSEC and arranged funding and donations for the OpenBSD Crypto Framework. At that same time I also did some consulting for the FBI, for their GSA Technical Support Center, which was a cryptologic reverse engineering project aimed at backdooring and implementing key escrow mechanisms for smart card and other hardware-based computing technologies.
My NDA with the FBI has recently expired, and I wanted to make you aware of the fact that the FBI implemented a number of backdoors and side channel key leaking mechanisms into the OCF, for the express purpose of monitoring the site to site VPN encryption system implemented by EOUSA, the parent organization to the FBI. Jason Wright and several other developers were responsible for those backdoors, and you would be well advised to review any and all code commits by Wright as well as the other developers he worked with originating from NETSEC.
From 2001 until 2003, it was funded by a grant from DARPA. Perry suggests that the reason OpenBSD lost its DARPA funding is that DARPA got wind of the FBI’s backdoors. At the time, de Raadt speculated that the funding was dropped due to antiwar statements he made in the press.
Perry also alleges that Scott Lowe, VMWare-Cisco Solutions Principal at EMC, is on the FBI’s payroll and that Lowe’s advocacy for OpenBSD VMs in enterprise VMware vSphere deployments is motivated by his connection to the FBI. Lowe denies this and told IT World:
Mr. Perry is mistaken. I am not, nor have I ever been, affiliated with or employed by the FBI or any other government agency. Likewise, I have not ever contributed a single line of code to OpenBSD; my advocacy is strictly due to appreciation of the project and nothing more
de Raadt writes that he published Perry’s e-mail so that:
(a)those who use the code can audit it for these problems,
(b) those that are angry at the story can take other actions,
(c) if it is not true, those who are being accused can defend themselves.
Wright responded via the OpenBSD mailing list. An excerpt of his response:
I will state clearly that I did not add backdoors to the OpenBSD operating system or the OpenBSD crypto framework (OCF). The code I touched during that work relates mostly to device drivers to support the framework. I don’t believe I ever touched isakmpd or photurisd (userland key management programs), and I rarely touched the ipsec internals (cryptodev and cryptosoft, yes). However, I welcome an audit of everything I committed to OpenBSD’s tree.
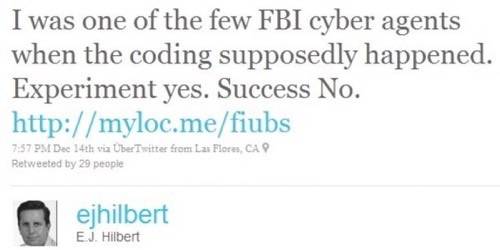
CNET’s Declan McCullagh spotted the following tweet from former FBI agent E.J. Hilbert:
Rob Beck, director of the OpenBSD Foundation, adds another level to the paranoid in this e-mail:
Is it simply a way to spread FUD and discredit openbsd?
Is it a personal gripe with the accused?
Is it an attempt to manipulate what is used in the market?
Is it outright lies
Is it outright truth and genuine altruism?
He also notes:
Of course in these days of binary only blob drivers, I don’t think the government need resort to this sort of tactic these days. Those nice binary-only drivers everyone loves running for video and wireless will ensure that there are nice places in your favorite Open Source project that can be coopted quietly by government organizations and have access to your entire kernel. No need to be subtle.
McCullagh’s CNET article includes a nice history of government snooping. I covered the subject for Disinfo a few years ago, including Julian Assange’s now defunct Rubberhose project.










