The clouds are aligning so to speak. Apps are everywhere. The variety of mobile devices connecting to the networks is unprecedented. In the process, identity management is becoming a major issue.
According to a Gartner survey earlier this year, enterprise managers see identity management as a top business priority. That would lead to the conclusion that enterprise operations are considering a variety of identity management options.
Emerging is a growing interest in social identity as a means for employees to sign into external applications.
Social identity is a new concept but it falls in line with technology adoption trends in the enterprise.
More so than ever before, companies are using social technologies for a variety of purposes – such as using Facebook as a customer service environment. Social identity serves as a way to manage all the various sites where people connect as part of their work.
Two examples include Facebook for Websites and Twitter, which uses OAuth, to verify the identity of the user. We are in the early stages but Facebook pages are pretty common so you can see why an enterprise may use it for employees to connect with third-party sites.
There’s another reason why social identity may have a lasting future. Federated identity has really not been adopted, leaving an opening for services with a social component.
It’s not that OpenID is going nowhere: Google Apps uses OpenID; it has been adopted to some extent by the federal government. But it is not nearly as popular as Facebook or Twitter.
But, still, these are very early days. And the issues are numerous.
Dion Hinchcliffe wrote on the topic earlier this year:
“Instead, off-premises SaaS and cloud computing offerings are offering basic synchronization with LDAP and other corporate identity repositories. Also becoming more and more important is identity authenticity (which Twitter tried to address with Verified Accounts). Watch for a raft of social identity issues to accumulate and for new enterprise open identity solutions to attempt to address them as our identities on the Social Web increasingly compete and conflict with our enterprise identities.”
Organizations are a long way from adopting social identity systems. OAuth 2.0 represents a first step as it automatically connects services. But there are other options, too.
Over the past several months I’ve had conversations with Eve Maler, one of the most authoritative voices about identity management. Eve is the chairman of the User Management Access Project Workgroup (UMA). UMA is proposal-as-a-service that would act as an intermediary platform for managing identities across social networks, SaaS providers and other services that the individual is responsible for managing. It gives more control to the user, who provides consent through the service.
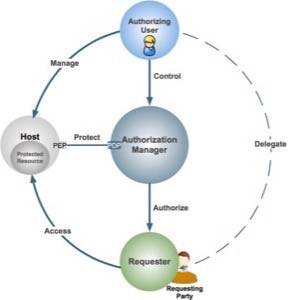
Phil Hunt writes:
“Where in the typical OAuth 2 deployment, user authorization and resource owner authorization are combined, UMA instead separates the processing of a user’s consent, from authorizing access by the resource owner (e.g. Flickr).”
Aside from the benefits Eve describes, here are a couple more things I like about the UMA proposal.
- UMA recognizes that user information exists in many places on the Internet, and not just at a single IDP/OPs etc.
- It supports a federated (multi-domain) model for user authorization not possible with current enterprise policy systems.
- It’s a great way to separate the issue of user consent away from the resource owner’s access control policy.
- It becomes possible to handle consent when individuals are offline.
Maler made the following point in response to Hunt:
“In the enterprise, an externalized policy decision point represents classic access management architecture, but in today’s Web it’s foreign. UMA combines both worlds with the trick of letting Alice craft her own access authorization policies, at an AM she chooses. She’s the one likeliest to know which resources of hers are sensitive, which people and services she’d like to share access with, and what’s acceptable to do with that access. With a single hub for setting all this up, she can reuse policies across resource servers and get a global view of her entire access landscape. And with an always-on service executing her wishes, in many cases she can even be offline when an access requester comes knocking. In the process, as Phil observes, UMA “supports a federated (multi-domain) model for user authorization not possible with current enterprise policy systems.”
Social identity makes sense for its ease of use. It fits with trends we see in the enterprise. The big question is trust and the implementation of infrastructures that provide a secure and simple way to identify the individual on the network.
In all, UMA may be a better answer for unified identity control across the enterprise and the Web.










